Runtime Application
Self Protection
(RASP)
Six Ways Approov Secures Mobile Apps
Approov provides the only comprehensive run-time security solution for mobile apps and their APIs, unified across Android, iOS, and HarmonyOS.






Mobile App Integration
Adding Approov to your iOS or Android app is easy. A wide range of platforms are supported using our Quickstarts below. The quickstart and SDK handles all of the interactions with the cloud service and implements a networking interceptor model that automatically adds an Approov token or secured API key to the required API requests. Dynamic Certificate Pinning is implemented automatically. The attestation process is managed automatically, refreshing as needed. After mobile app integration, you register each app version with the Approov command line tool.
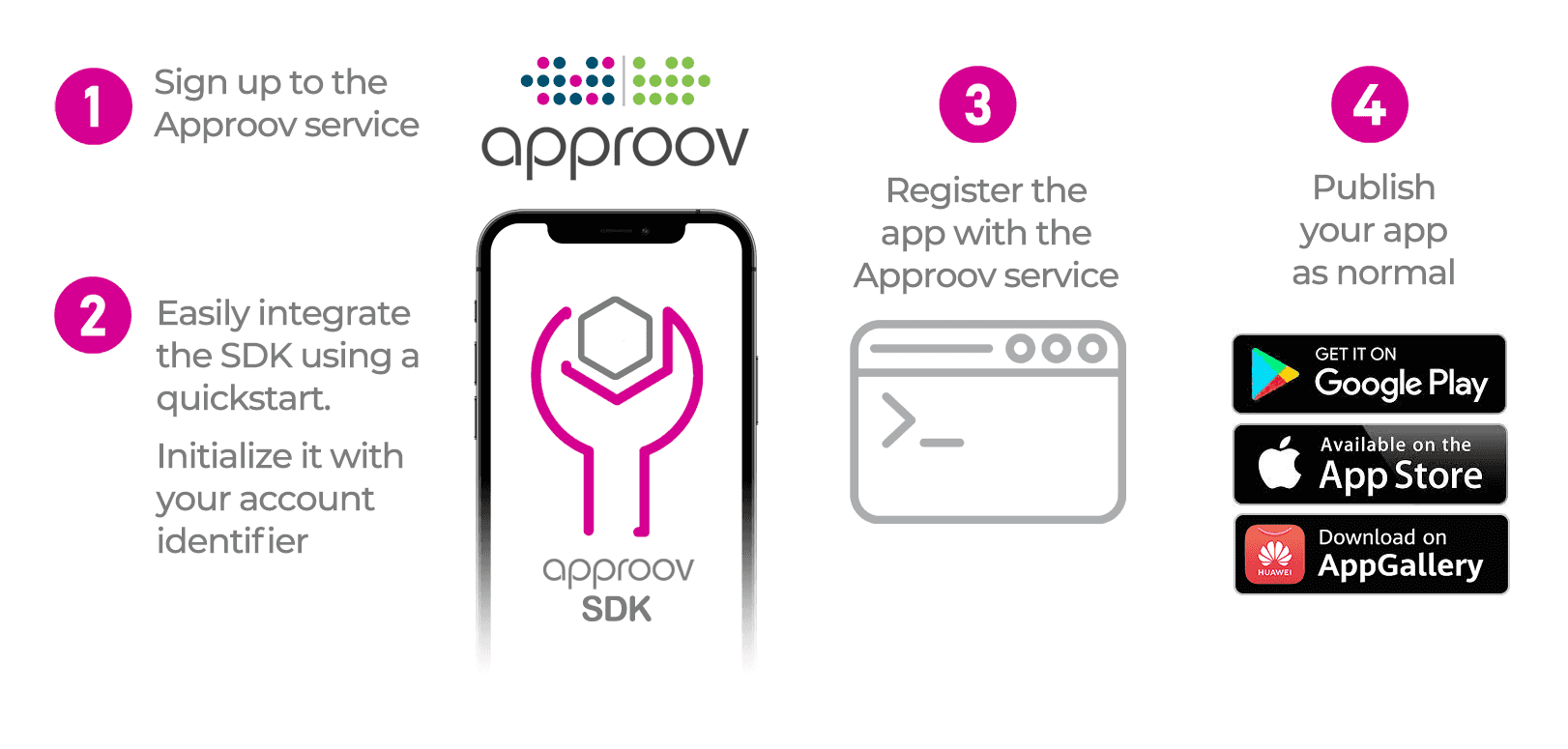
Mobile App Quickstarts
Quickstart guides are provided for popular developer platforms below. If your platform is not listed, see Direct SDK Integration or Contact Us







