FHIR Vulnerabilities Press Release

U.S. Healthcare’s “Last Mile” is Open to Attack, New Study Finds; Approov Rolls Out FHIR Guard, Free End-Point Security for FHIR API Providers
In “Playing With FHIR” Report, Cybersecurity Researcher Alissa Knight Reveals Major “Last Mile” EHR Security Issues in Healthcare Apps - Millions of Patient Records are Exposed.
SAN JOSE, CA and EDINBURGH, UK, October 13, 2021 - Approov, creators of advanced API threat protection solutions, today issued new research findings in, “Playing with FHIR - Hacking and Securing FHIR APIs,” by cybersecurity researcher Alissa Knight on the security vulnerabilities of the fast healthcare interoperability resources (FHIR) APIs studied and the mobile apps which access them. The research reveals that healthcare FHIR APIs, even when designed in accordance with FHIR guidelines, are nonetheless subject to abuse by automated scripts and compromised apps.
Approov also introduced Approov FHIR Guard, a complimentary new API security as a service offering to shield EHR vendors’ and aggregators’ FHIR APIs. FHIR Guard helps FHIR API providers incent and assist their “downstream” partners in implementing stronger cybersecurity measures that reduce the risks in “last mile” healthcare mobile app security issues.
"An effective kill chain in the targeting of the healthcare industry will not be one targeting the EHR systems running in the provider’s network, but targeting the third-party FHIR aggregators and third-party apps which access these EHR APIs. It is alarming how sensitive patient data moves from higher security levels to third-party aggregators where security has been found to be flagrantly lacking,” said researcher Alissa Knight.
Among key findings in “Playing with FHIR – Hacking and Security FHIR APIs” are:
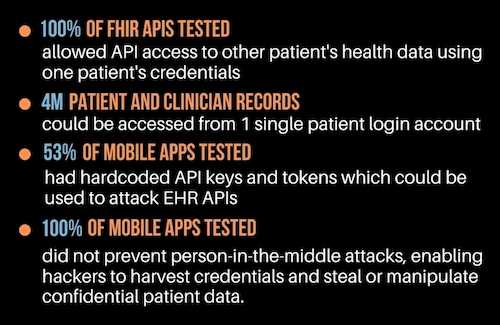
- 3 production FHIR APIs serving an ecosystem of 48 apps and APIs were tested
- The ecosystem covered aggregated EHR data from 25,000 providers and payers
- 4m patient and clinician records could be accessed from 1 single patient login account
- 53% of mobile apps tested had hardcoded API keys and tokens which could be used to attack EHR APIs
- 100% of FHIR APIs tested allowed API access to other patient's health data using one patient's credentials
- 50% of clinical data aggregators did not implement database segmentation allowing access to patient records belonging to other apps developed on their platform for other providers
- 100 percent of the mobile apps tested did not prevent person-in-the-middle attacks, enabling hackers to harvest credentials and steal or manipulate confidential patient data
The College of Healthcare Information Management Executives (CHIME) concurs. In a press release welcoming the recent FTC clarification that non-HIPAA covered third-party apps will be covered by the Health Breach Notification Rule, CHIME Policy Steering Committee Co-Chair Scott MacLean said, “We at CHIME advocated directly for the expansion of the personal health record definition and for the utilization of the FTC enforcement authority in comments to the agency last year, and we are happy to see our concerns directly addressed. Patient data safety is crucial for maintaining trust in the patient-provider relationship, and ensuring that patients’ data remains safe even when they are outside of the four walls of the hospital only helps strengthen that bond.”
The report’s three recommendations to address these major “last mile” security gaps are:
- Secure Authorization: App developers and EHR aggregators must follow best practices as custodians of patient data - including implementing authorization scopes, app attestation, secure channels, and pentesting.
- Block Non-Compliant Apps’ Access to Sensitive Data: Healthcare and EHR providers should carefully monitor EHR access through FHIR APIs and develop enforceable certification programs for EHR data aggregators and app developers, and must also be prepared to apply the Security Exception to the Cures Information Blocking Mandate to players who do not comply with security best practices.
- Chain of Custody: The ONC should require EHR access through FHIR APIs be fully secure at every step from the EHR provider to the patient or any other EHR consumer, and establish and enforce this chain of custody through legal and financial accountability
In February 2021, Approov and Knight released, “All that we let in,” research which revealed that 100 percent of the 30 popular mHealth apps tested were proven vulnerable to API attacks allowing access to full patient records, PHI and PII. Approov has continued to sponsor Knight’s research on the unintended consequences of the latest push to open APIs in healthcare. Knight’s current focus includes the mandating of Substitutable Medical Applications, Reusable Technologies (SMART) on FHIR by the ONC Cures Act Final Rule as the means to facilitate an open ecosystem for sharing protected healthcare data.
“We see it as a positive step that open APIs are already creating a plethora of healthcare services which are being adopted and appreciated by patients and consumers,” said David Stewart, CEO, Approov, Inc. “However, healthcare organizations and regulators who handle and oversee this sensitive data must give equal attention to security enforcement as they do to empowering citizens to take control of their patient data. With this research we don’t just want to raise a red flag. The introduction of FHIR Guard is a genuine effort by Approov to contribute positively towards improving the situation today, ahead of regulations which will surely follow in time.”
The 21st Century Cures Act mandates that all patients be able to electronically access their health information. SMART on FHIR version 4 was standardized as the API used to integrate and provide access to patient EHR records. Though not covered by HIPAA, companies must disclose breaches promptly. The FTC can and will levy fines. The new report reveals that the security of EHR records requested by the end user/patient is very weak even if API security is well-defined and EHR vendor systems were well implemented. “Last mile" security - between HIPAA-compliant EHR systems and the patient – is woefully inadequate and must urgently be addressed to close the gap.
Knight recommends in the report: "Put in place app and device attestation checks in your API endpoints and require any apps connecting to your endpoint to implement this control. The Approov solution effectively prevented my malicious traffic from reaching API endpoints."
The full report, “Playing with FHIR - Hacking and Securing FHIR APIs,” can be downloaded here.
Approov’s FHIR Guard Blocks “Last Mile” Attacks - Free for FHIR API Providers
Approov FHIR Guard puts in place controls in the API endpoint to be able to protect the API and stop the threats described in the report. App owners who choose to integrate Approov will pay per use for the service. Approov prevents bots, scripts and compromised apps from:
- using stolen user identity credentials
- exploiting vulnerabilities in APIs
- malicious manipulation of the business logic of the APIs
- executing Man-in-the-Middle attacks
- complimentary API security solution for “last mile” security
Approov offers the solution and deployment assistance of the end-point protection element free of charge to FHIR API providers who deploy production FHIR APIs handling real patient data. This makes it easy for 3rd parties downstream of the APIs to deploy Approov and augment the security of their apps by putting in place app and client attestation to better protect the channel to the end-user.
You can confirm that your organization is eligible to deploy Approov FHIR Guard by emailing FHIRGuard@approov.io.
Upcoming Webinar
Alissa Knight will present the results of the research in a live webinar on October 28th. You can register here for the webinar.
About Approov
Approov solutions help stop API abuse at the edge, and prevent security breaches in mobile channels. With more businesses moving to digitalization and future-ready services that utilize mobile API connections, securing those connections properly can get overlooked or not fully implemented for all possible threats, exposing organizations and their users to breaches, fraud, denial of service, and other forms of API abuse.
Approov API Threat Protection provides a multi-factor, end-to-end mobile API security solution that complements identity management, endpoint, and device protection to lock-down proper API usage. It ensures that only safe and approved apps running in safe environments can successfully and securely access an organization’s APIs, and turns away unauthorized accesses by attacker scripting, bots and fake or tampered apps. https://www.approov.io/
Media Contact
Dan Chmielewski
Madison Alexander PR, Inc.
714-832-8716
C: 949-231-2965
dchm@madisonalexanderpr.com

