How to Prevent Mobile Man-in-the-Middle (MitM) Attacks

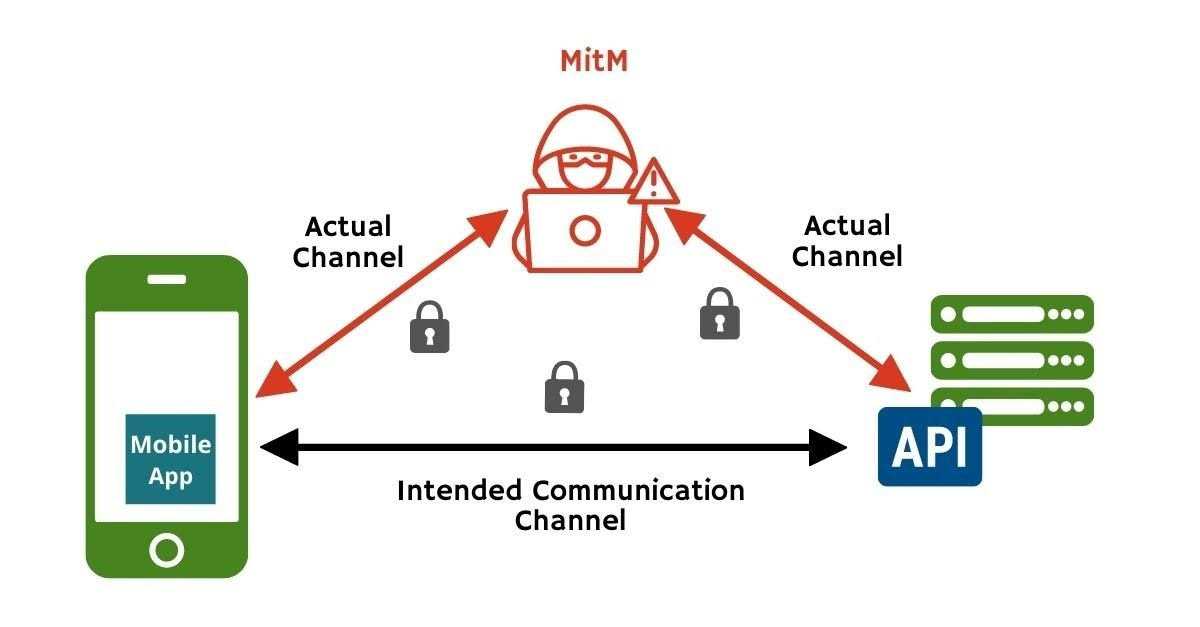
The communication channel between apps and APIs presents a rich target for hackers via Man-in-the-Middle (MitM) attacks. Transport Level Security (TLS) alone is not sufficient to stop them since tools installed in the device can easily intercept encrypted communications.
This free whitepaper provides an in-depth analysis of the techniques used by hackers and explains how certificate pinning can help thwart mobile MitM attacks. It also introduces methods to prevent hackers tampering with device environments.
In addition, it shows how over-the-air updates can be employed to reduce the chance of customer service being interrupted. Certificate rotations can be handled instantly and cleanly, eliminating any need to update apps.
Request Your Copy Now
Whitepaper Contents
- Introduction
- Man in the Middle Attacks
- TLS and Encrypted Traffic
- The Chain of Trust
- Breaking Trust - Trust Store Poisoning
- Breaking Trust - CA Breach
- The Benefits of Pinning
- Public Key Pinning versus Certificate Pinning
- Implementing Pinning
- The Static Pinning Configurator
- The Operational Risks of Pinning
- The Bad News - Pinning Can Be Bypassed in the Client
- Pinning Bypass by App Repackaging
- Pinning Bypass Using a Hooking Framework
- Certificate Transparency
- Dynamic Pinning Provides Easy Administration and Elimination of Operational Risks
- The Final Piece in the Puzzle - How to Block Client-Side MitM Attacks
- Approov: Complete MitM Protection with Assured Service Continuity
- Conclusion

