Runtime Application
Self Protection
(RASP)
Six Ways Approov Secures Mobile Apps
Approov provides the only comprehensive run-time security solution for mobile apps and their APIs, unified across Android, iOS, and HarmonyOS.

App Attestation
Approov definitively attests to the authenticity of your app and the device on which it is running.

Real Time
Threat Intelligence
Approov gives you direct real time insight into your deployed apps, the environments they are running in and any threats being actively defended.

Dynamic Certificate Pinning
Approov's blocks Man-in-the-Middle (MitM) attacks and enables secure over-the-air instant pin updates without service disruptions.

Runtime Secrets Protection
Approov allows removal of hardcoded API keys and secrets from your app. These can be updated instantly across installed apps.

API Security
Approov protects your backend APIs from API abuse, credential stuffing, fake botnet registrations, and DDoS attacks.

API Shielding
Approov detects unsafe operation environments on the client device, such as rooted/jailbroken devices, debuggers/emulators and malicious frameworks.
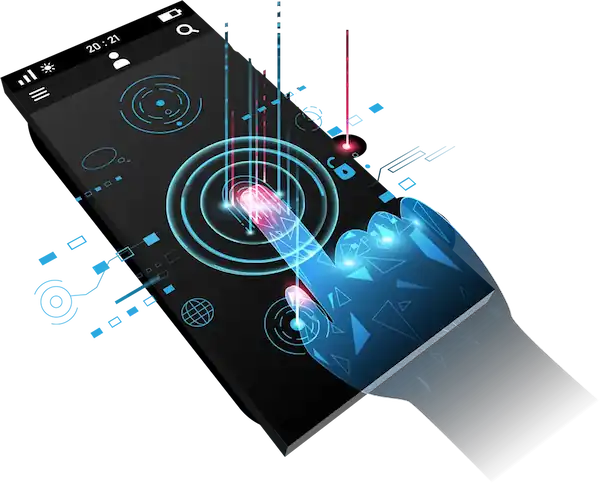
Mobile App Integration
Adding Approov to your iOS or Android app is easy. A wide range of platforms are supported using our Quickstarts below. The quickstart and SDK handles all of the interactions with the cloud service and implements a networking interceptor model that automatically adds an Approov token or secured API key to the required API requests. Dynamic Certificate Pinning is implemented automatically. The attestation process is managed automatically, refreshing as needed. After mobile app integration, you register each app version with the Approov command line tool.

Mobile App Quickstarts
Quickstart guides are provided for popular developer platforms below. If your platform is not listed, see Direct SDK Integration or Contact Us.
Related Resources
How to “Zero Trust” Your: Mobile devices, Mobile Apps, Cloud-to-Device Channel, Attribution, Authentication
Request a Demo
Give us 30 minutes and our security experts will show you how to protect your revenue and business data by deploying Approov to secure your mobile apps.