App
Attestation
.png)
App Attestation
App Attestation is a runtime technique used to provide proof that an app is truly authentic and running in a trusted device. It uses a combination of measurements made on the client but checked by a remote attestation server.
Benefits
Migrate security decisions into the cloud for greater security and flexibility
Token based cryptographic security with no secrets in the app
Optional integration of platform attestation for additional security
Definitive Attestation
Traditional app security approaches integrate all of the threat detection logic into the app itself, which is running in an attacker controlled environment. Even if the detection code is well defended, it relies on the app making a local decision about it’s own integrity, which presents an obvious weak point that is frequently exploited by attackers.
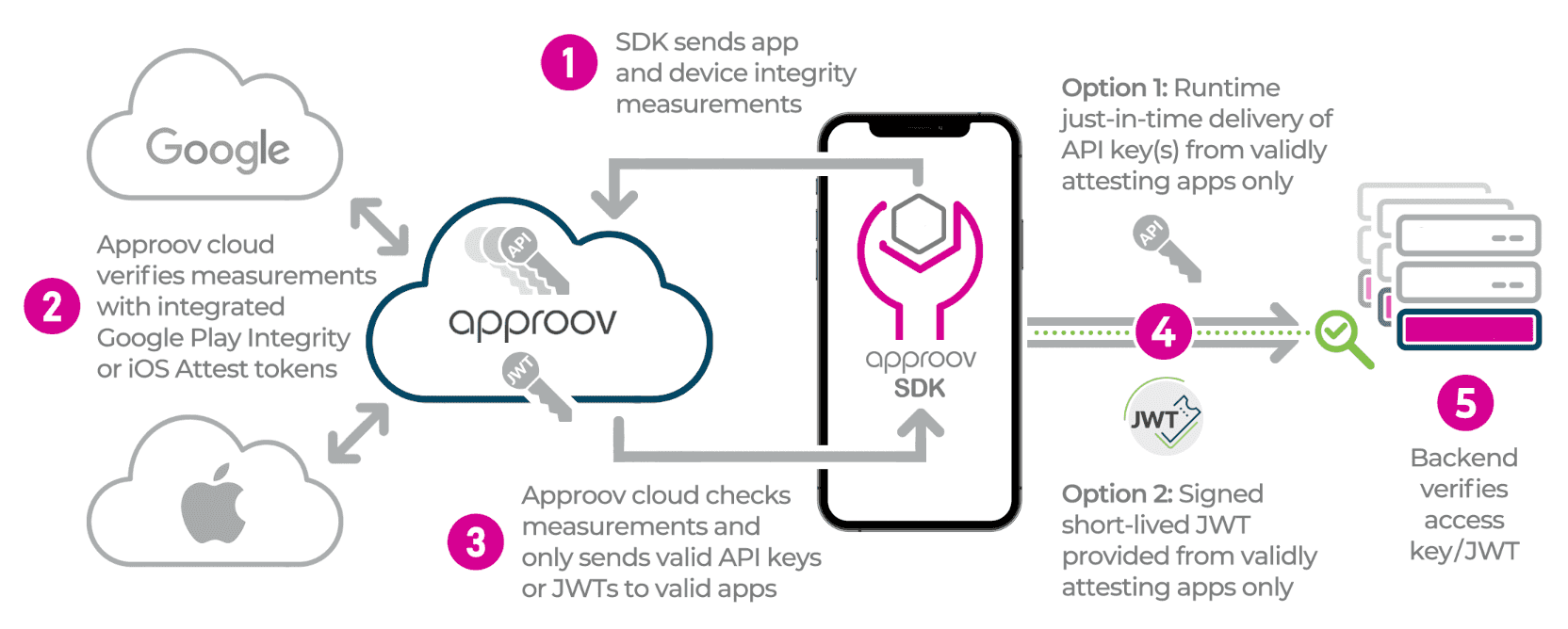
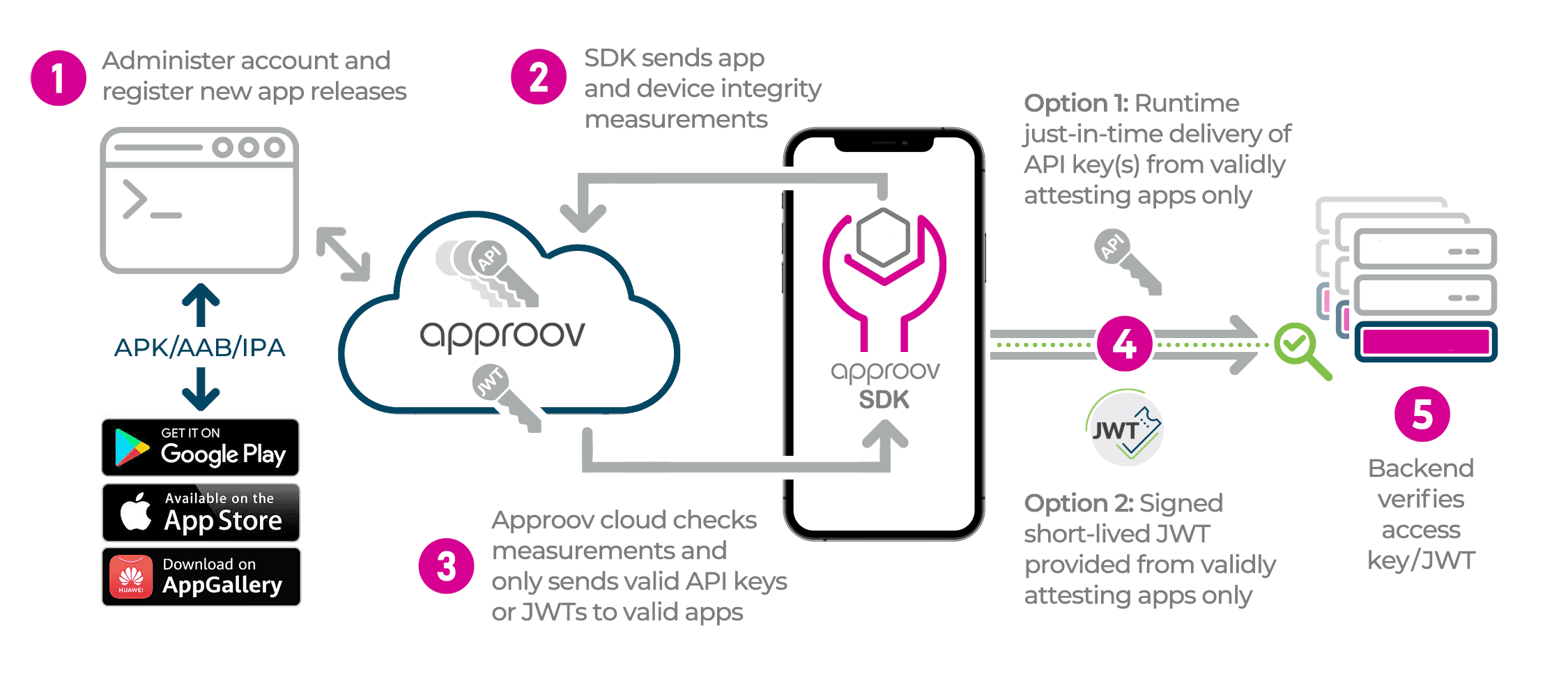
Approov is different. It uses a remote attestation approach, where the running app must prove itself to be genuine through a sequence of integrity measurements. These results are then sent to the Approov cloud service using a patented challenge-response protocol, immune from replay attacks. The Approov cloud makes the decisions.
If integrity is verified then the running app is issued with a short lived cryptographic token that it can use to prove its authenticity to the backend API services it uses. The app cannot make its own decisions about integrity and cannot sign its own tokens. Defense is moved out of the attacker’s reach and into the Approov cloud.
Google Play Integrity and iOS App Attest Integrated
Approov provides more granular control, wider device support, cross-platform consistency and various other advantages over the basic platform capabilities. However, Approov does optionally integrate with iOS App Attest / DeviceCheck and Google Play Integrity to provide the most comprehensive attestation and powerful threat management framework.