Stop AI Scraping
of Mobile APIs at the Edge

Approov App Attestation Turns Scraping From a Detection Problem, to a Cloud-Enabled Security as Standard
Agentic AI can reverse-engineer apps, replay API calls, and harvest structured data at scale. Approov protects your data by requiring cryptographic proof that requests come from your genuine app running in an acceptable environment—before any data is returned.

Why AI Scraping is Different Now
Scraping moved “downstack”: from HTML pages to mobile APIs.
Detection doesn’t scale: AI agents adapt, rotate infrastructure, and mimic legitimate traffic patterns.
The root cause is trust: most backends authenticate users, but don’t verify the app instance sending the request.
If your backend can’t prove “this request came from your genuine mobile app,” then any actor who can reproduce your API calls can extract data.
Developer-First Design
Approov Stops AI-Scraping Across Industries
Marketplaces & Retail
Stop cloned apps and scripts from harvesting SKUs, undercutting prices, or abusing drops and promos.
Ticketing & Events
Protect ticket inventory from automated polling, resale intelligence, and unfair purchase advantages.
Travel & Booking
Prevent mobile API bypass that enables price intelligence, inventory abuse, and automated trip agents.
Property & Listings
Prevent large-scale scraping of listings, pricing, availability, and market signals.
Data Service
Ensure structured data is accessible only to genuine app users—not automated or cloned clients.
Gaming & Gambling
Prevent bots and scripts from exploiting gameplay, bonuses, odds, and player accounts.
Financial Services
Secure mobile APIs against automation, credential abuse, and data exfiltration.
Healthcare
Secure sensitive mobile APIs against automated access and data harvesting.
How Approov Stops AI Scraping
Approov performs ongoing inspection of your app and the device environment and issues a short-lived, signed JSON Web Token (JWT) that represents the app attestation result. Your app includes it with requests; your backend verifies it before serving sensitive endpoints.
Your App Fetches an Approov Token
The SDK performs integrity measurement and works with the Approov cloud service.
Approov Issues a Short-Lived Signed JWT
Token represents the attestation outcome.
Token is Added to API Requests
Approov can automatically add the token as a header for protected API domains.
Backend Verifies the Token
Verification is straightforward using standard JWT libraries.
Security Policy Enforcement
Valid → allow. Invalid/missing → block, rate-limit, or step-up, based on your individual preferences.

Without Approov
Trust Based on Credentials Only
Detection After Data is Returned
Reactive Response
Scraping Visibility is Poor

With Approov
Trust Based on App Authenticity
Access Denied by Default
Prevention at the API Boundary
Clear Enforcement Signal
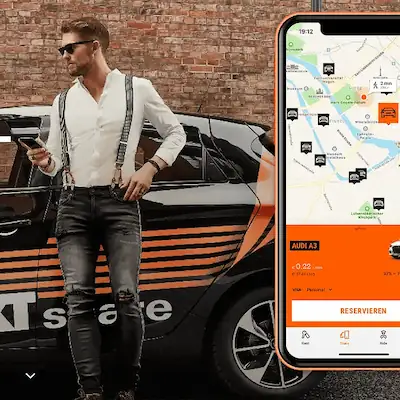
How Approov has helped stop mobile app scraping
Car rental company Sixt was looking to protect customer data and prevent competitors from accessing information about their availability, pricing and promotions.

Why Teams Think They're Protected, But are Actually Vulnerable
“We use OAuth,
so we’re safe”
OAuth authenticates users, not apps.
“We don’t see
abnormal traffic”
Scraping traffic is designed to look normal.
“Our APIs
are private”
Mobile APIs are discoverable once an app is shipped.
“TLS pinning
stops this”
Pinning protects traffic in transit, not request replay.
If Any of These are True, Reassessment is Warranted
“We don’t see scraping in our logs — doesn’t that mean we’re safe?”
“Doesn’t TLS pinning or certificate validation stop this?”
“We authenticate users — why isn’t that enough?”
“Can’t we just rate-limit or detect bad behavior?”
“If someone reverse engineers our app, can’t we just rotate keys?”
“Does app attestation block legitimate users or partners?”
“Is this really a problem outside of very large companies?”
Where Complete App & API Security is Required
Make mobile API scraping impossible, not just detectable. Meet with our experts to learn more, or see for yourself with a complementary trial.
