Runtime
Secrets
Protection
%20(1).webp)
Runtime Secrets
Runtime Secrets is an innovative technology that allows API keys and other secrets to be completely removed from the app package shipped to the app store. Instead, secrets are securely delivered to valid app instances at runtime, improving the security posture and providing significantly enhanced operational flexibility.
Key Benefits
 Eliminate Secrets
Eliminate Secrets
Migrate your dangerous hardcoded secrets from app packages into the cloud where they can be securely managed
 Operational Flexibility
Operational Flexibility
Improved operational flexibility by rotating secrets on demand
 Implement with No Changes
Implement with No Changes
Implement with no changes needed to backend APIs
Want to see the power of Approov in action?
Other Features of Approov End-to-End Mobile App Security
Want to learn more about Approov?
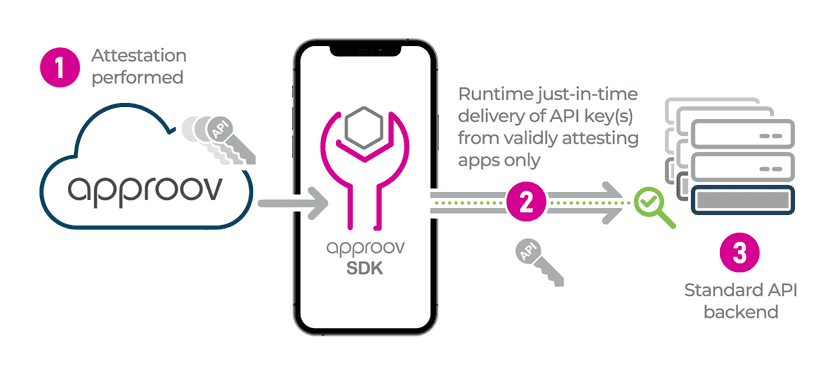
Just-in-Time Secrets from the Cloud
Approov Runtime Secrets Protection can be used to protect and manage all the secrets a mobile app uses, including API keys used to authenticate against various backend services. With Approov you no longer need to hardcode these in your app, where they were both fixed and subject to reverse engineering extraction.
The Approov cloud service delivers secrets “just-in-time” to the app only at the moment they are required to make an API call, and only when the app and its runtime environment has passed attestation. This ensures that sensitive secrets cannot be extracted from the app package or via Man-in-the-Middle (MitM) attacks.
Secure Secrets Delivery

Dynamically Managed
Shift left with Approov and integrated runtime secrets management, giving you complete operational flexibility and observability. Rotate secrets as needed and eliminate the risk of secrets exposure damaging your business.
All secrets are stored by the Approov cloud service and are easy to manage dynamically. Certificates, pins, and API keys can easily and immediately be updated across all deployed apps. In this way, if secrets are ever stolen from cloud repositories or acquired through other means, or if a third-party API used by your app changes keys, they can immediately be rotated without any service interruption and without having to update apps.
Secured Remote Configuration
Some approaches exist whereby an app can receive secrets and other configuration from a remote server. This removes the secrets from the app and allows dynamic updates of the configuration but it isn't secure. An attacker can send a request to the endpoint to get the secrets. Moreover, the secrets are not safe once they reach the mobile app without tamper and communication channel protections.
Approov provides a unique combination of remote configuration capability along with advanced app protections. This ensures that secrets can only ever be delivered to authentic apps that have proved they are not being manipulated.
Request a Demo
Give us 30 minutes and our security experts will show you how to protect your revenue and business data by deploying Approov to secure your mobile apps and your.
Get a Trial
Approov offers a complimentary 30 day trial (no credit card necessary) to give you immediate and valuable insight into the security risks of your mobile apps and the devices they run on.
Related Resource

PDF Document
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadInfographic
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadTemplate
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadGuide
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadCourse
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadWebinar
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadData sheet
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadVideo
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadBlog post
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadWhitepaper
A description of the resource being shared. Just a couple of sentences should be just right.
DownloadCase study
A description of the resource being shared. Just a couple of sentences should be just right.
Download