Here at Appoov, we were wondering why there has been so little discussion about applying the principles of Zero Trust specifically to mobile apps when this is a concept which has become quite mainstream in enterprise security.
We believe Zero Trust is very applicable to the security of mobile applications and discussed it with the cybersecurity experts at TAG Cyber. They wrote an ebook which explains why this is important and more importantly how you can start applying Zero Trust principles in order to take the security of your mobile apps to a new level.
In this blog I want to provide a short introduction to the Zero Trust approach and summarize why it makes sense for mobile apps and the APIs they use. You can read the TAG Cyber ebook here.
What is Zero Trust?
Zero Trust security is an increasingly important way for organizations to protect their data. Overall, this method requires device, user and network verification for access to corporate resources — and always only providing the minimum access necessary. Basically, trust is never implicit.
Large enterprises, small businesses and government organizations are all evaluating and implementing Zero Trust. In fact, United States Executive Order 14028 now requires government agencies and their suppliers to set up a Zero Trust architecture.
Zero Trust is a model that recognizes that a simple, one-time authentication and authorization process is not sufficient because changes in user behavior, location and the like can radically impact access decisions. Zero trust enforces minimal access to resources, and requires continuous security monitoring, risk-based access control, and continuous authentication and authorization based on real-time information.
Zero Trust protects data in real time even as the threat environment evolves.
Zero Trust dates back to 2009, when John Kindervag, who was with the analyst firm Forrester, came up with the idea that networks should be designed without implicit trust, enforcing strict identity verification and least-privilege access policies for every user, device, or application, regardless of whether they are located. In the same year, Google introduced BeyondCorp, a security framework which shifted the focus from protecting the perimeter to individual devices and users, thus dramatically reducing the potential attack surface for future hackers.
The idea that a modern enterprise no longer has a perimeter to protect gave the idea its momentum.
Fast forward to today and every enterprise security vendor promotes a version of “Zero Trust” and NIST has adopted and promotes the concept as a best practice. US Government guidelines now “requires agencies to achieve specific zero trust security goals” and the US DoD has also published a ZT Strategy Document.
One thing that is notable is that these documents and recommendations do not contain any specific focus on mobile apps. This could be seen as a gap in the guidance, especially considering:
- The unique challenges mobile apps present (e.g., diverse operating systems, BYOD scenarios, app store ecosystems)
- The growing role of mobile apps in storing and accessing sensitive enterprise data and personal information
- The specific security concerns related to mobile apps such as data leakage, malware, insecure data storage, app cloning
Organizations implementing Zero Trust should consider how to apply the principles specifically to their mobile app ecosystem, even if the high-level guidance doesn't provide detailed mobile-specific recommendations.
How to Apply Zero Trust to Mobile Apps
Let's take a look at some of the key elements of Zero Trust and how we can apply them to the mobile environment. This involves adapting the core concepts of Zero Trust architecture to the unique challenges and environments of mobile applications.
- Use a Single Integrated Framework: The first step of a ZT approach aims to identify the most critical data, assets, applications, and services and develop security policies for each. As part of this process you should specifically address mobile app interactions. This includes defining how data should be protected both within the app and during transmission to backend services.
- Never Trust and Always Verify: Implement strong authentication mechanisms, such as multi-factor authentication (MFA), to verify the identity of users and devices accessing the mobile app. Use runtime app and device attestation as an additional protection to provide continuous contextual verification of the integrity of the app and the device for every access request to the API.
- There Is No Enterprise Perimeter: Treat all mobile devices as potentially untrusted, regardless of whether they are within the corporate network or not. Ensure that security measures are applied consistently across all devices and continuously evaluate client environments for threats.
- Continuous Run-Time Monitoring of Everything: Continuously monitor the behavior of the mobile app and the device it runs on. Use runtime application self-protection (RASP) to detect and respond to threats in real-time.
- Assume Breach: The "assume breach" mentality in ZT encourages organizations to prepare for potential security incidents, acknowledging that breaches can happen regardless of preventive measures. ZT recommends organizations should have established protocols for quickly addressing breaches, such as revoking access, quarantining affected systems, and conducting thorough investigations. For mobile, continuous monitoring and verification help mitigate the impact of security incidents. In addition it is critical to be able to react immediately: to update policies as threats evolve, to isolate compromised apps and devices, and rotate keys and certificates should breaches occur.
By adhering to these key premises, organizations can effectively implement a Zero Trust architecture that expands to mobile protection, enhances their security posture, reduces the risk of data breaches, and ensures that sensitive resources are protected.
Approov Applies Apply Zero Trust to Mobile Apps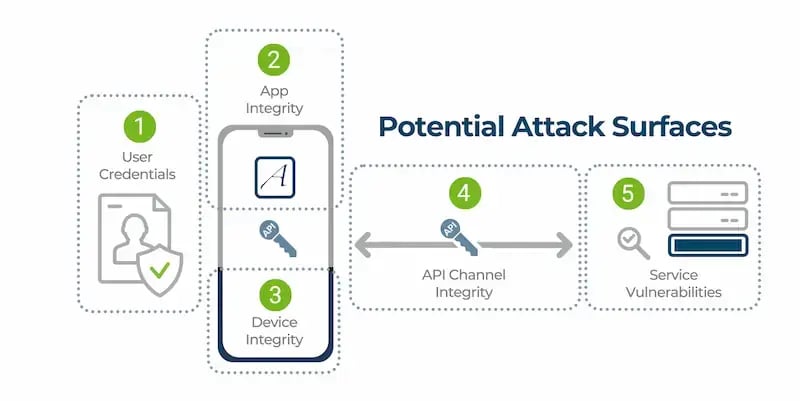
With Approov, every single call to an API from the mobile app includes a confirmation that the app is genuine and unmodified and that the environment the app is running in has not been manipulated. Approov RASP continuously validates the app and the device environment and prevents any scripts, bots and modified or repackaged mobile apps from abusing an API by using stolen user credentials or API keys.
Approov layers robust cryptographic methods and dynamic certificate pinning on top of network security layers to prevent Man-in-the-Middle attacks and provides dynamic API key protection to defend against the theft and abuse of API credentials.
Approov policies can be updated in real-time, and monitoring provides continuous visibility. When security incidents occur, suspicious devices can be blocked, API keys and certificates can be rotated immediately and service can be maintained.
Approov are experts on the security of mobile apps and their APIs and we can help you extend your Zero Trust Architecture to mobile apps and devices.

George McGregor
VP Marketing, Approov
George is based in the Bay Area and has an extensive background in cyber-security, cloud services and communications software. Before joining Approov he held leadership positions in Imperva, Citrix, Juniper Networks and HP.





