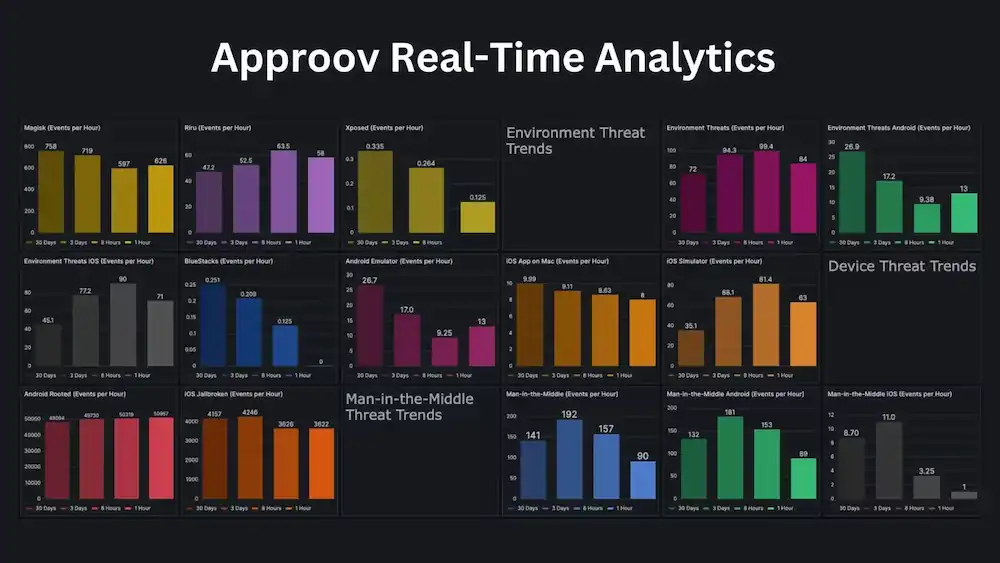
Mobile apps and APIs are increasingly being targeted by cybercriminals using sophisticated techniques to exploit vulnerabilities and gain access to sensitive data. To stay ahead of these threats, real-time analytics on the security state of mobile apps and devices is critical.
Mobile app security solutions like Approov can provide invaluable real-time insights through its mobile attestation capabilities. By running on-device tests in real-time, Approov can detect if a mobile device has been compromised through jailbreaking, rooting, malware infection, while also making sure the channel is not compromised via man-in-the-middle attacks or other vectors.
Going beyond just static malware scanning, Approov dynamically analyzes the integrity of both the device and the mobile app in its operational context. This allows security teams to identify in real time, sophisticated API attacks like reverse engineering, hooking, emulators, code tampering and more (see Figure 1).

Figure 1: Riru, GameGuardian, Magisk, Xposed, Frida and Cydia are all tools that can be used to modify or "hack" Android or iOS apps and devices. These attacks are detected by the Approov Mobile Attestation framework and blocked from accessing data through the APIs.
The detailed attestation reports provide actionable data including the specific reason an attestation check failed. Security teams can use these real-time analytics to identify compromised devices accessing APIs, block fraudulent transactions, and take corrective actions.
Here are some of the threats identified by Approov:
- Riru and Magisk are both tools that can be used to gain root access on Android devices. This gives the ability to fully modify the operating system.
- GameGuardian is an app that can hook into other apps to modify values, bypass in-app purchases, cheat at games, etc.
- Xposed is a framework that enables "modules" to tap into and modify system and app processes on a device.
- Frida is a dynamic instrumentation toolkit that can inject scripts into apps to monitor behavior, bypass security controls, etc.
- Cydia is an alternative app store for jailbroken iOS devices that allows installing hacked apps and tweaks.
With real-time visibility, mobile app vulnerabilities and malware infections can be detected quickly before any major damage is done. Analytics empower security teams to identify anomalies in mobile app behavior and pinpoint misuse of credentials or session hijacking attempts.
For example, Approov’s Threats Detected/Stopped Today dashboard shows the specific threats identified and blocked in the last hour and current day. This includes data on jailbreaking, app tampering, and man-in-the-middle attacks (see Figure 2).
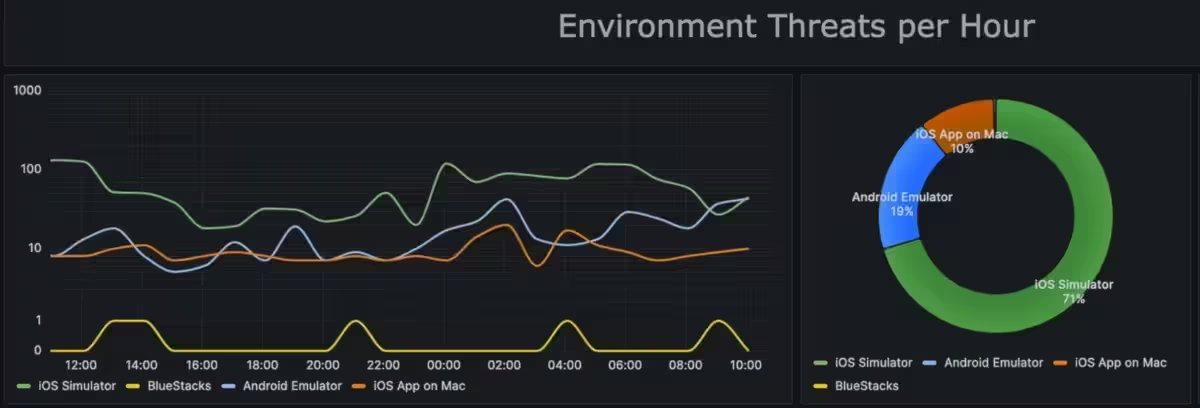
Figure 2: Real-time telemetry on emulator and simulator threats is incredibly useful for mobile developers. It offers timely, actionable insights to identify API abuses and fortify defenses against ever-evolving attack techniques targeting mobile apps.
Getting real-time analytics on threats like emulators, Bluestacks, iOS simulators has immense value for mobile security developers protecting APIs:
- It provides visibility on potentially malicious traffic to APIs coming from unauthorized tools instead of real devices. Emulators can be used to reverse engineer and scan APIs.
- Analytics identifying emulator usage allows blocking API access to maintain integrity. Prevent unwanted data scraping, bot traffic, and other abusive activities.
- Trend data on increasing emulator usage may indicate an emerging campaign targeting APIs, prompting further investigation.
- Detecting iOS simulators could mean developers are attempting to reverse engineer iOS apps and tamper with app behavior prior to re-packaging.
- Usage stats on tools like Bluestacks help identify attacks originating from PCs/laptops masquerading as mobile devices to fly under the radar.
- Otherwise legitimate tools like emulators can be misused by bad actors. Analytics aid in differentiating benign vs malicious usage.
- Real-time detection capabilities allow immediate action to block identified emulator traffic at API edge. Prevent attacks before any damage is done.
- Data on geographical distribution and frequency of emulator usage provides clues on hacker targeting and where to strengthen defenses.
- Over time, analytics establish baseline "normal" emulator usage to highlight anomalies indicative of new threats.
- Provides evidence to demonstrate risk of emulator-based attacks to business stakeholders and justify additional security investments.
The Threats by Category dashboards visualize the evolution of different threat types on Android and iOS over time. This provides crucial insights into new attack campaigns and trends.
Unlike static application security testing, Approov provides ongoing attestation of the device and app integrity throughout the software lifecycle. This ensures the mobile app's security posture is continually analyzed even after updates or changes. Security policies can be updated and new rules can be pushed to the device without the need to re-release a new app through the app store.
![]()
With mobile threats continuing to grow in scale and sophistication, real-time telemetry and continuous verification are crucial. Approov's mobile attestation analytics allow organizations to take data-driven actions to defend their mobile apps and APIs from the latest threats. It offers timely, actionable insights to identify API abuses and fortify defenses against ever-evolving attack techniques targeting mobile apps.

Ted Miracco
CEO of Approov
Ted’s high-technology experience spans 30 years in cybersecurity, electronic design automation (EDA), RF/microwave circuit design, semiconductors, and defense electronics.