At a time when the world could use some good news, any good news, the central health crisis continues to get compounded by a persistent wave of cyberattacks targeted at companies and their employees. Not even healthcare institutions and agencies at the center of responding to the emergency have been spared, with the World Health Organization, the U.S. Department of Health and Human Services and even a UK-based coronavirus testing facility being targeted by cyber profiteers.
Then, in a rather grisly pretence of compassion, some of these cybercrime groups proclaimed that healthcare and medical organizations would be off target. No respite, however, is on offer for the rest of the world’s institutions and citizenry.
Just between February and early March this year, coronavirus-related cyberthreat indicators escalated by over 600%. One study in Italy even found that companies with broader adoption of work-from-home policies experienced a sharp increase in phishing and weaponized email attacks. Apart from intensity, the nature of the threat itself continues to evolve in terms of technical prowess and sophistication as remote work opens up a number of new cyberattack vectors.
The first step to addressing this exigency is to understand the broad characteristics of these attacks. According to one analysis, the widespread interest in COVID-19 is being leveraged for a range of malicious campaigns including email spam, BEC, malware, ransomware and malicious domains. The number of coronavirus-related spear-phishing email attacks have also spiked significantly, from just 137 in January to 9,116 in March.
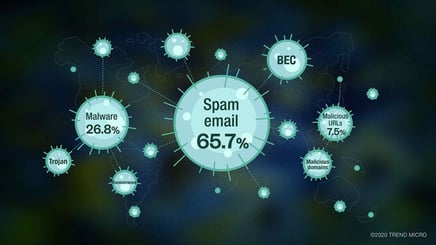
Source: Trend Micro

Source: Barracuda
Securing against COVID-19 threats
The vulnerability of people trying to come to terms with a crisis, rather than technology, is the focal point of almost all of these campaigns. Threat-aware employees, therefore, have to be the first line of defense against cyber intrusions.
Take phishing for instance, an exploit that accounted for nearly a third of all attacks in 2019. And yet, 38% of untrained users, up from 30% in 2019, will fail realistic phishing scenarios. Awareness training, therefore, has to top the list of priorities for organizations to secure critical corporate resources in a distributed work model. Employees have to be educated on the precautions that must be taken while dealing with spam, phishing and other social engineering scams.
This basic training also needs to educate people of the basics of technical hygiene. Start with password security training and the importance of not only using strong passwords but also using different passwords across different devices/services and Wi-Fi connections.
Emphasize the need to use only secure Wi-Fi networks and require the use of VPNs before signing on to unsecured networks. Businesses have to ensure that VPN solutions have been tested for both security and capacity and where required provide performance-focused VPN connections for critical work.
Enforce a consistent layer of multi-factor authentication with biometric identifiers. Use data encryption and ensure that all communication applications such as chat and email use end-to-end encryption. Ensure that firewalls, antivirus and anti malware software are updated.
Finally, review cybersecurity policies to cover the immediate demands of remote work including access management, the use of personal devices and data privacy considerations.
Preparing for a new norm
The concept of remote work, mobile work forces and distributed teams is not entirely a new or unexpected phenomenon. The diffusion of traditional IT perimeters has been underway for quite some time now. The shift to cloud-first IT and the rising preference for a more flexible work schedule among a younger generation of employees has prompted many companies to provide support for a mix of remote and on-premise work. In fact, most knowledge workers believe that the traditional office setting could become obsolete by 2030.
What the current situation has tested is businesses ability to engineer this transformation at a pace and scale that was unprecedented. Among many observers, this short-term large-scale experiment may well result in remote work becoming the norm.
However, facilitating this flexible distributed model has to be done without compromising security. And enabling an extended, large-scale and secure shift presents some unique access and security considerations that cannot be addressed by standard security appliances or by awareness training and technical hygiene.
For instance, cloud based-app are a key component in any efficient and productive remote working model. Today, large companies are deploying 163 apps on average, at a deployment rate that has increased 68% over the past four years. It is a similar story with mobile apps where more and more companies are publishing internal employee-facing apps to public app stores. In fact, one study found that Fortune 500 companies were the most active when it came to publishing employee apps, accounting for 72% of internally facing apps.
Now, these apps are proliferating because they are an inherent part of a truly digital workplace and offer significant value both to the enterprise and its employees. However, these apps do make it easier for bad actors to exploit holes in networks.
Take mobile apps for instance. Most modern apps use APIs to interact with remote services and APIs in general are becoming a rich target for hackers. Mobile APIs can be abused in several ways, including compromising certificate authority and stealing API keys, to deliver a range of threats including MiTM attacks, data scraping, credential stuffing, app impersonation and DoS/DDoS attacks. Businesses, therefore, have to take a unified approach that emphasizes the golden triad of “verified user, verified channel, and verified app” in order to ensure effective API security.
A similar “never trust, always verify” principle will be central to securing an enterprise whose well-defined IT perimeter has been blurred by concepts such as remote work. With no “edge” to secure, it is no longer possible for a centralized command and control structure to manage access control across users, devices, applications and endpoints. In this Zero Trust security model, the perimeter is wherever an access control decision has to be made. And that, combined with heightened security awareness and technical hygiene, is what will enable companies to embrace the concept of remote work without compromising security.
To sum up, the mandatory transition to remote work, and the consequent cyberattacks, occasioned by the current crisis have preempted some of the security challenges of the distributed work model. There is an opportunity, however, for organizations to learn from this imposed experience to prepare for a future where, by most accounts, remote work will be the norm.
David Stewart
Advisor at Approov / Former CEO of Approov
30+ years experience in security products, embedded software tools, design services, design automation tools, chip design.






