An OWASP AppSec California 2019 Talk
ShipFast and ShipRaider made a return appearance at the sixth annual OWASP AppSec California as defender and attacker in Preventing Mobile App and API Abuse.
AppSec California is a terrific conference, with interesting talks and attendees, and did I mention it is held on the beach in Santa Monica in late January? Most presentations were video taped, including my own here:
As ShipFast launches its mobile app with hidden API keys and OAuth2 user authorization, we start by discussing the existing security threats and how to counter them. Along the way, TLS, certificate pinning, HMAC call signing, app hardening, white box crypto, app attestation and more will strengthen ShipFast’s security posture, but ShipRaider will also be working hard trying man in the middle attacks, app decompilation and debugging, exploit frameworks, and other reverse engineering techniques to keep exploiting ShipFast’s API. This fast-paced overview of mobile attacks and counter-measures demonstrates the defense in-depth techniques required to protect both your mobile apps and your API backends.
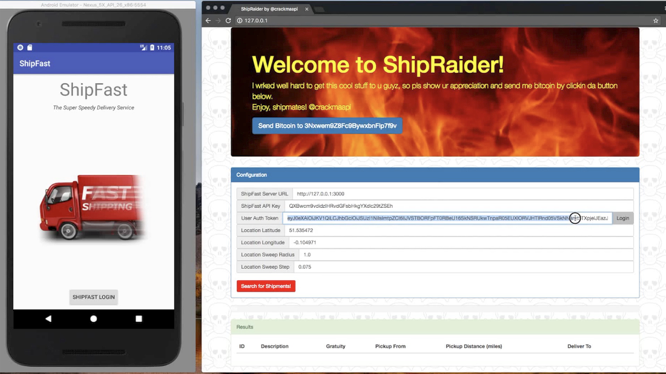
ShipFast and ShipRaider are open-sourced by CriticalBlue and are available on github including some additional attack-defense scenarios. You’ll walk away with access to a fully worked open source example and some additional homework assignments if you want to go deeper. A more thorough overview of mobile API protection may be good preparation for working through the material.

Skip Hovsmith
Senior Consultant at Approov
Developer and Evangelist - Software Performance and API Security - Linux and Android Client and Microservice Platforms








