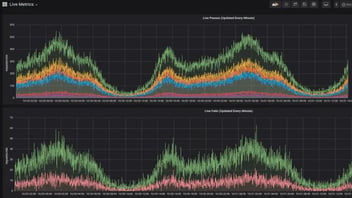
API abuse, when the API is used in an unexpected way, is a growing problem in software development and one of the leading attack vectors cybercriminals exploit. According to a recent security research report that surveyed more than 200 enterprise security professionals, there was a 21.32% growth in malicious API call volume between December 2020 and December 2021. The same study also established that 95% of respondents had suffered an API security incident in the past year.
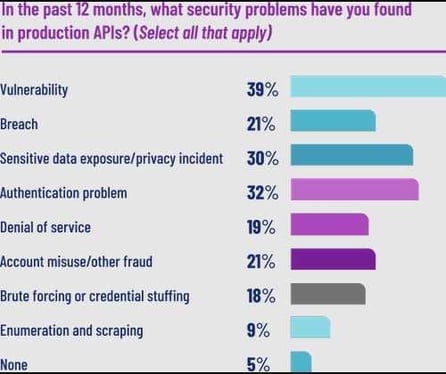
Source: Salt Security
Examples of API Abuse
Some typical examples of ways that APIs are abused include:
- Man in the Middle attacks: Attackers can use Man in the Middle (MitM) attacks to intercept communications between the app and the backend server. Once communications are intercepted, valuable or sensitive information may be seized and/or manipulated in order to use gain access to backend servers via the API.
- Repackaged or modified apps: Hackers can modify an existing app to include malicious code. The modified app then makes calls to the API to allow the attacker to access sensitive data or to convince genuine users to use the compromised app.
- Scripts or bots: Criminals can use scripts or bots to automate requests to the API in order to scrape data, apply compromised credentials, or overload the system. This is the most common form of API abuse and can lead to denial of service conditions among other conditions which will impact legitimate API users.
- Reverse engineered apps: Attackers can reverse engineer an app to discover the secrets it uses to access its API and the business logic contained within the app. The bad actor can then use this knowledge to make unauthorized calls to the API.
Why is API Abuse a Serious Issue?
Some of the reasons that API abuse is a major threat for organizations include:
- Lack of Awareness: One of the biggest challenges in preventing API abuse is that many organizations are simply unaware that it’s a problem. They may not have experienced an attack yet or may not be monitoring with sufficient granularity to detect this kind of suspicious activity. Specifically, many organizations lack the means to differentiate between a genuine user and a script/bot.
- Mobile Apps are a specific Security Threat: Mobile apps are one of the most common attack vectors for API abuse. It is estimated that there are more than five million apps in the Google Play Store and Apple App Store combined. Unfortunately, many of these apps have poorly written code that attackers can exploit, and even those that don't can still be reverse engineered such that their APIs can be abused.
- DDoS Attacks are on the Rise: Denial of service attacks (DDoS) are a common type of attack that nefarious actors can use to take down an online service. Botnets often launch these attacks, which are networks of infected computers that attackers control. In a DDoS attack, the attacker sends a large number of requests to the API to overload the system and cause it to fail.
Preventing API Abuse
Organizations whose business relies heavily on mobile apps can take several steps to prevent API abuse. Further, they should take care to protect all five of the mobile attack surfaces.
- Monitoring and Logging: Organizations should monitor for suspicious activity on their APIs. They can do this by looking for unusual patterns in the traffic, such as many requests from a single IP address. In addition they should incorporate mechanisms to detect when API requests are automated.
- Rate Limiting: Rate limiting is a security measure that limits the number of requests that an IP address can make to an API in a given time. This helps prevent bots and other automated programs from making too many requests and overwhelming the system, although it should be remembered that a low frequency script will likely get past rate limiting.
- Authentication and Authorization: Organizations should require authentication for all API calls. They should also use authorization to control what data or actions a user can access.
- Certificate Pinning: APIs should use SSL pinning to ensure the API communications can't be sniffed by man-in-the-middle attacks. Dynamic certificate pinning is an implementation of pinning which is easy to deploy and manage because certificates/pins can be updated directly into running apps without requiring new app version to be uploaded to the app stores.
David Stewart
Advisor at Approov / Former CEO of Approov
30+ years experience in security products, embedded software tools, design services, design automation tools, chip design.






.jpg?width=352&name=Vampire%20Piggy%20Bank%20(1).jpg)