We got together with our friends at Quokka recently to talk about securing the mobile application software development lifecycle and why it's important to get a dynamic feedback loop going between the security approaches you use at different stages of the life cycle. This blog presents some of the highlights of the recent webinar.
A good place to start with mobile app security is to do two things: deploy a leading Mobile App Security Testing (MAST) solution to eliminate threats prior to rollout and to put dynamic Mobile Runtime Application Self Protection (RASP) in place to get visibility to runtime threats and block them in real time.
But the real opportunity is to connect the two to really elevate your security posture.
Quokka are experts in MAST and Approov in mobile RASP so who better to drive a lively discussion about security across the lifecycle? You can watch the recording of the discussion, where we cover ways to improve security end-to-end, reduce DevSecOps costs and mitigate the risk of costly breaches.
Prioritizing Mobile App Security
Security teams are struggling to balance the need to prioritize their organization’s most critical security risks, while also protecting against attacks at their weakest points.
Unfortunately, this means many organizations have not allocated enough resources to protecting mobile apps – their newest threat vector with a rapidly expanding attack surface. Verizon’s 2023 Mobile Security Index report states, "Mobile app threats rose over 30% from early 2022 to 2023," and "up to 90% of cyberattacks and 70% of data breaches start at endpoint devices."
There are cost-effective methods to protect against this rapid rise in mobile threats. Organizations developing mobile apps need to proactively remediate zero-days throughout the SDLC and dynamically protect their apps at runtime.
Getting Started - Review the Standards and Best Practices Which Apply
As a first step you should review the relevant standards and compliance requirements for your particular industry. These can cover specific defenses and testing as well as detailed breach reporting requirements. In finance, there is PCI, for US Healthcare complying with HIPAA is critical. If you're working in the US government space you probably have to comply with the NIA.
For useful resources and tools, there are two sources in particular we would highlight. NIST provides a framework for security through the lifecycle. The NIST Cybersecurity Framework (CSF) 2.0b allows enterprises to better understand, assess, prioritize, and communicate cybersecurity efforts, from planning all the way to recovery should things go wrong.
OWASP covers app, API and mobile security. OWASP MAS compliments NIST as a particularly relevant and active community specifically for mobile app security. The OWASP MAS project provides robust and up-to-date resources for developers and security professionals alike.
The overall Mobile Application Security Verification Standard (MASVS) was simplified last year.
And this year the OWASP Mobile App Top 10 and the Mobile Application Security Testing Guide (MASTG) have been updated and a brand new Mobile App Security Weakness Enumeration (MASWE) tool has been added.
Key Mobile Risks to Consider
There are two fundamental problems with mobile apps: The first is that they can be reverse engineered, even if attempts have been made to obfuscate code. The second is that they run in a client environment which is neither owned nor controlled by the app owner.
Unless steps are taken, mobile apps can be analyzed, understood, cloned or copied, and the environments they run in can be hacked, rooted, instrumented and manipulated to interfere with the operation of an app.
Before you even deploy an app, you should aim to be secure by design and bake that into everything you do.
By employing automated tools like Quokka MAST, you can look for known or potential vulnerabilities and to help remediate them. It's also critical to evaluate the software supply chain and verify any code that you're bringing into the app. One common issue uncovered by scanning is data leakage, where sensitive information is inadvertently exposed through logging or other means.
When it comes to runtime there are five primary attack surfaces that organizations must protect:
- User Credentials: Protecting user credentials is paramount. Even with multi-factor authentication, stolen credentials can lead to credential stuffing attacks.
- App Integrity: Ensuring that the app accessing APIs is genuine is critical, especially with the rise of sideloaded apps and alternative app stores.
- Device Integrity: The environment in which the app operates can be hostile. Tools and software can interfere with app functionality, creating vulnerabilities.
- Communication Channels: Even with encryption, attackers can intercept traffic using tools like mitmproxy, making it essential to secure communication channels.
- API Vulnerabilities: Third-party APIs can introduce risks if not properly secured. OWASP publishes a Top 10 list of API vulnerabilities that organizations should be aware of.
The patented run time protection solution from Approov validates each request to backend APIs, ensuring that only genuine applications can access sensitive data. This not only protects the 5 runtime attack surfaces but also provides real-time visibility into the app’s performance and potential threats.
Getting Started with MAST and RASP
There are two things you can do quickly:
- First, scan your app with a MAST solution like the one from Quokka. By doing this, businesses can quickly identify vulnerabilities and prioritize remediation efforts and inject security into the development process.
- Second, put runtime security from Approov in place to add Zero Trust protections against runtime attacks and gain visibility to new threats.
For MAST, it's simple to upload your app binary to the Quokka service or scan your app directly from an app store. You will immediately see detailed findings and guidance on how to address the most urgent issues. The Quokka solution categorizes risks as critical, high, medium or low and you can tune the risk criteria for your particular industry and use-case. To get started, you don't try to boil the ocean: you can start by solving two or three of the highest category issues.
Approov is easy to deploy and once in place, you register your application with Approov before you put it into the app store. At runtime, every time there's a request to the backend APIs, the Approov SDK checks the authenticity of the app and it analyzes the runtime environment and it looks for hooking tools and debugging tools and anything that is nasty that's in the device environment. All that data and measurements is passed to the Approov service which then decides whether it's valid or not and passes a token back to the Approov SDK which then integrates that into the request to the back end.
First Priorities and an Easy Win
One of the high category issues you will no doubt uncover from your first scan is that you have API keys or secrets in your code. Numerous studies have found secrets exposed in widely deployed apps in both Apple and Android app stores. Even if your own code is clean, often libraries used in app code expose secrets.
One thing you can do immediately with the Approov solution is you can get those API keys out of your code. This will quickly solve a lot of issues.
Because of the unique way Approov acquires attestation information about the device and the application, API keys can be delivered just in time to the application but only when the device and app are verified as genuine and unmodified.
Using Quokka to perform that first scan and and Approov to remove any exposed API keys is a simple first step which has immediate benefits and will radically improve your security profile: this is an “easy win” as far as security is concerned.
Achieving a Continuous Security Approach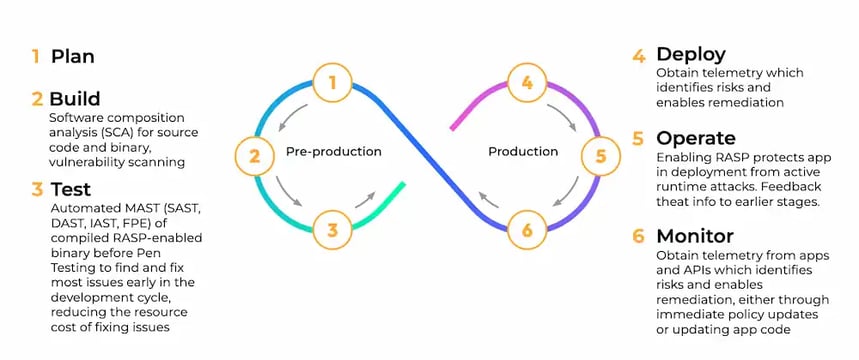
Security is not a one-time effort but a continuous process. Adopting a zero-trust approach to mobile app security is key. This involves constant monitoring of the app and its environment, ensuring that any emerging threats are promptly addressed. You can then use that to feed back in the tools that you're using upstream and it's very important to put in place the mechanisms and the processes to be able to do that.
Frequent use of automated security testing is a crucial component of this approach. Anytime anything changes, a new series of automated mobile app security tests should be carried out, including static and dynamic analysis.
Remediating issues is not a one-time thing either because you need to be looking for evolving risks and new threats as they appear. Approov shows in real time what device, app and man-in-the-middle attacks are happening and gives you the actionable intelligence that you're going to need.
If (When) Things Go Wrong
Zero trust says “assume breach”. You need to do scenario planning and you must rehearse the procedures you will follow when there is a breach. NIST helps with guidelines for this. A good recent example of not being prepared was the breach of 23andme - the company gave the impression of not having a solid plan in place.
Most important is ensuring service continuity and this should drive your choice of security solutions.
One example of how to think about this concerns API keys. Breaches of API keys are common and if you are not ready to rotate these quickly, service continuity can be impacted.
With Approov, secrets are stored by the Approov cloud service and are easy to manage dynamically. Certificates, pins, and API keys can easily and immediately be updated across all deployed apps when required. When keys are stolen, or if a third-party API you use decides to change keys - Dropbox being a good recent example of this - they can immediately be rotated without any service interruption and without having to update apps.
In Summary
As mobile applications continue to play a pivotal role in business operations, securing them against evolving threats is imperative. By understanding the risks, adopting a continuous security approach, and leveraging advanced tools, organizations can protect their mobile applications and maintain user trust.
For more insights on mobile app security and best practices, be sure to follow the Approov blog and the Quokka blog. Together, we can navigate the complexities of mobile security and seize the opportunities it presents.

George McGregor
VP Marketing, Approov
George is based in the Bay Area and has an extensive background in cyber-security, cloud services and communications software. Before joining Approov he held leadership positions in Imperva, Citrix, Juniper Networks and HP.






