Five Pillars of Effective Mobile API Security
App Integrity
Don't:Allow your API keys to be used by bots, scripts and fake apps to access your backend data and services
Do:Attest your apps to ensure only truly authentic apps are authorized to make API calls
Device Integrity
Don't:Allow your app to run in compromised environments which can expose vulnerabilities and exfiltrate sensitive data
Do:Adopt comprehensive fine-grained device integrity checks enforced outside of the untrusted device environment
Channel Integrity
Don't:Allow man-in-the-middle attacks by assuming that plain TLS is good enough
Do:Employ securely certificate-pinned TLS with dynamic pin update
Credential Integrity
Don't:Allow scripts to access your APIs and conduct credential stuffing attacks on your login endpoints
Do:Require frequent app authentication for strong trusted user and API authorization
Service Integrity
Don't:Allow zero-day threats to compromise your defenses and rely on new app releases to update protections
Do:Shield your APIs from exploitation of vulnerabilities with over-the-air updates for instant reaction to threat intelligence
How API Attacks Impact Your Business
Account Takeover
Fake Account Creation
Denial of Service
Credit Fraud
App Impersonation
Man in the Middle
API Security Breach
Scraping
Form of identity theft using techniques like session hijacking, password cracking, or credential stuffing using mass log in attempts to verify the validity of stolen username/password pairs.
Introducing Approov
How Approov Protects Your Business
- Data breach mitigation - ensures only genuine mobile app instances, running in safe environments, can use your API.
- API abuse prevention - blocks all scripts, bots, modified apps and fake apps from exploiting your API.
- Instant protection - integrates easily into your existing technology stack.
- Fraud reduction - provides immunity from the most common API attacks.
Free eBook • Generic API Security Backgrounder
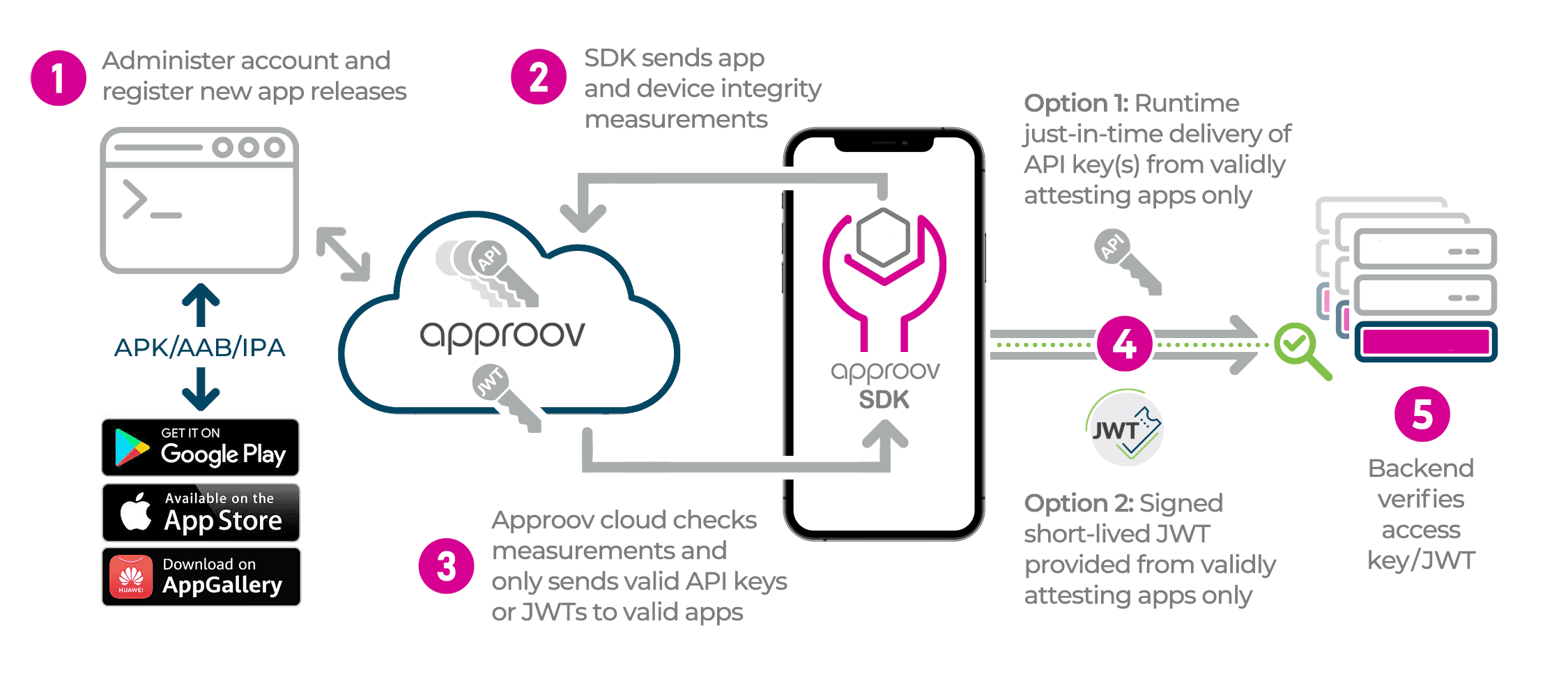
How Approov Works
Approov consists of three components:
- Approov cloud service which makes all security decisions off device - delivers uncompromisable security
- An SDK that drops into your iOS or Android app - delivers fast deployment
- Short-lived security tokens to authenticate API traffic at your backend - delivers rapid time to protection
App and device integrity are checked repeatedly every five minutes. Channel integrity is checked continuously.
Only apps that have been registered with the Approov service and which meet the runtime environmental criteria are issued with valid JWT Approov tokens.
Approov JSON Web Tokens (JWT) are signed with a custom secret only known to the Approov cloud service and the backend API. The secret is never contained within the app itself, so it cannot be extracted.
App registration can be immediately added and revoked from the Approov service, allowing tight control of which app versions can access your API.
App and device integrity are checked repeatedly every five minutes. Channel integrity is checked continuously.
Only apps that have been registered with the Approov service and which meet the runtime environmental criteria are issued with valid JWT Approov tokens.
Approov JSON Web Tokens (JWT) are signed with a custom secret only known to the Approov cloud service and the backend API. The secret is never contained within the app itself, so it cannot be extracted.
App registration can be immediately added and revoked from the Approov service, allowing tight control of which app versions can access your API.
Approov Capabilities
Positive app attestation
Man-in-the-middle rejection
User authorization binding
Dynamic certificate pinning
Easy app SDK integration
JWT backend token verification
Selective security policies
DeviceCheck integration
SafetyNet integration
Emulator detection
Debug detection
Root detection
Jailbreak detection
Magisk detection
Frida detection
Xposed detection
Cydia detection
Clone app detection
App automation detection
Memory dump detection
Real-time metrics
Over-the-air security updates
DevOps tooling
24/7/365 support
Free 30-Day Evaluation • Access to All Features • No Credit Card Needed • Immediate Protection
Integrate Your App
Integrating Approov into mobile applications is straightforward, and quickstart guides are provided for the popular platforms:
After integration Approov tokens are automatically added to your API calls. The integration handles all of the analysis and measurement necessary to identify the app and the runtime environment to the Approov Cloud Service.
After integrating the SDK into your app, register each app version with the Approov Cloud Service using the Approov command line tool. This extracts and registers the “DNA” of the app with the cloud service so that your app can be positively attested. Your app is then published as normal, and the enhanced security is transparent to your users.
Free 30-Day Evaluation • Access to All Features • No Credit Card Needed • Immediate Protection
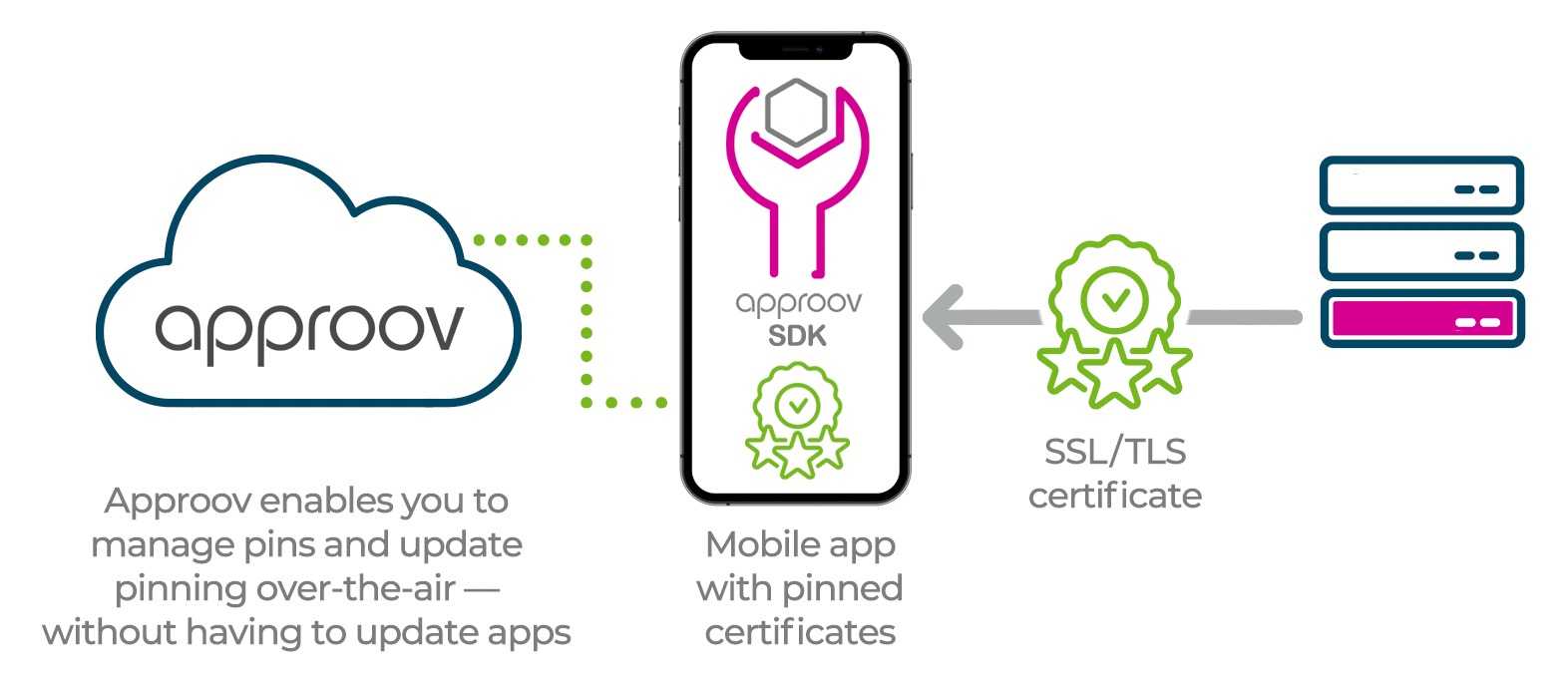
Pin Your API Connections
Even though modern apps communicate using a secure TLS connection they are still vulnerable to eavesdropping by a Man-in-the-Middle (MitM) attacker. Such attacks are used to reverse engineer an API protocol.
Employing certificate pinning prevents such attacks. Unfortunately, this can be complex to implement in the app and requires coordination with the backend API services. Approov builds pinning right into the integration with support for updating pinning over the air with no app update needed. Certificate rotations can be handled cleanly, with no risk of interruption to your customers.
Free 30-Day Evaluation • Access to All Features • No Credit Card Needed • Immediate Protection
Verify Your API Traffic
Integrating Approov into backend services is straightforward too, and quickstart guides are provided for popular platforms:
Token verification is simple due to the adoption of the industry standard JWT. You simply check that each token has been correctly signed with the secret for your account, and that it has not expired.
Once the SDK has been integrated into your app, live tokens are added to your API request headers, and your backend API systems are enhanced to verify these tokens.
Free 30-Day Evaluation • Access to All Features • No Credit Card Needed • Immediate Protection
Operate With Confidence
We continuously use the aggregated and anonymized data that we have from all of our customers to identify new threats and enhance Approov's security capabilities accordingly.
Monitor and Analyze Attestation Traffic
Live metrics are accumulated regarding device usage, attestation forensics, and billing information. Both graphical and email based reporting is available.
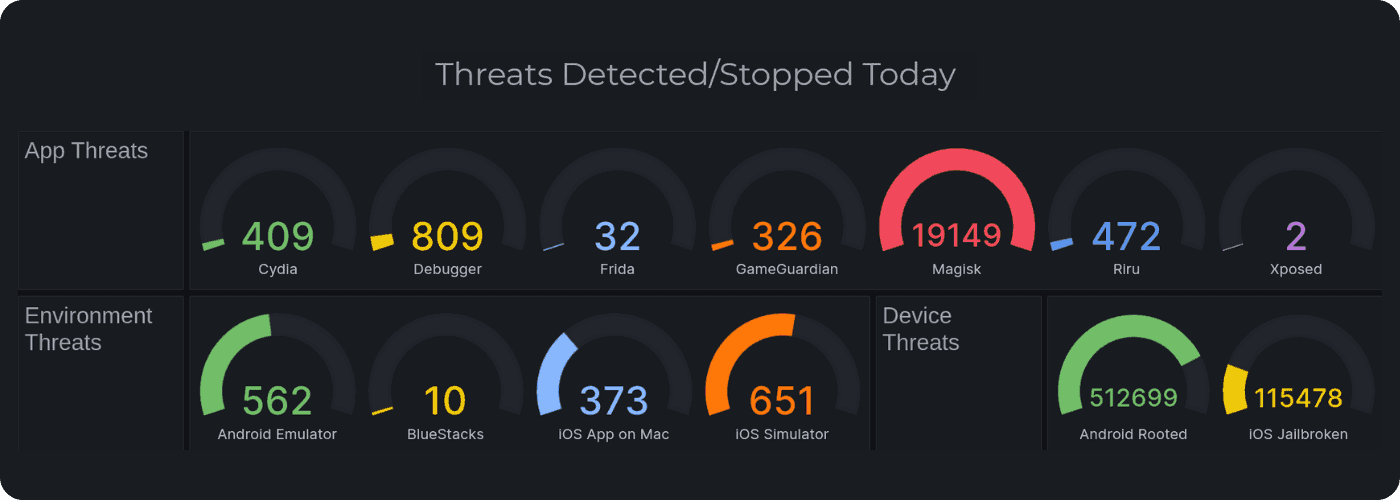
Update Your Security Live
Approov detects potentially unsafe mobile device environments including device rooting/jailbreaking, emulator or debugger usage, malicious instrumentation frameworks, and cloned apps. Customers specify which policies should be enforced. Changes to security policies roll out immediately to active apps.
Hackers continuously evolve their run time penetration techniques, and Approov keeps pace by providing security detection updates over the air without requiring app store updates. This live update service is also used to manage trust certificates and security policies.
Free 30-Day Evaluation • Access to All Features • No Credit Card Needed • Immediate Protection