David Stewart
- Advisor at Approov / Former CEO of Approov
30+ years experience in security products, embedded software tools, design services, design automation tools, chip design.
![]()
This is the final article in our 3 part review of trends in the Mobility market. In case you missed them, the first part can be found here and the second part can be found here.
In 2015, “white hat” hackers remotely attacked a Jeep Cherokee and left it paralyzed on the side of a highway. They returned in 2016 with an in-vehicle hack to prove that things could get much worse. In 2017, researchers from an IT security company analyzed some of the most popular mobile apps from car manufacturers to find that every app was vulnerable to attacks in some shape or form. In 2018, the number of Black Hat attacks overtook White Hat incidents for the first time in the history of Smart Mobility.
In 2019, a security researcher discovered hard coded credentials inside the mobile app of a popular vehicle telematics system that left tens of thousands of cars vulnerable to hackers. The same year, another researcher told a magazine how he could immobilize 25,000 cars at the push of a button.
Automotive cybersecurity incidents have increased sevenfold since 2010, according to a Global Automotive Cybersecurity Report 2020 from automotive cybersecurity firm Upstream Security, and doubled over the last year. Every segment in the smart mobility ecosystem, including OEMs, consumers, commercial vehicles, car-sharing services and governments, has been exposed to hacks and cybersecurity incidents. And every possible attack vector has been exploited; with keyless entry/start-engine systems, servers, and mobile apps emerging as the most prevalent.
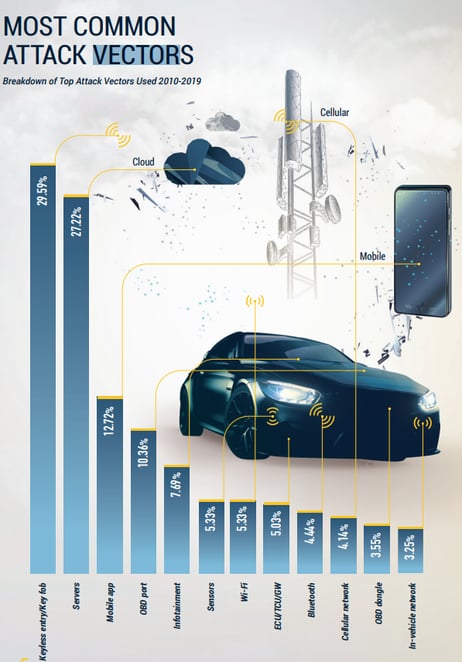
SOURCE: Upstream Security
A Synopsys-SAE International survey of professionals responsible for contributing to or assessing the security of automotive components found that a clear majority had concerns about cybersecurity practices not keeping pace with the ever-evolving threat landscape. Almost a third of the respondents revealed that their companies lacked an established product cybersecurity program or team and nearly two-thirds said that less than half of the hardware, software and technologies were tested for vulnerabilities.
Modern cars are virtually mobile data centers incorporating multiple servers, ECUs, sensors and more lines of code than a modern fighter jet. All this complexity expands the attack surface for bad actors and will only get worse as automotive connectivity expands to a V2X (vehicle to everything) model where every car communicates with other vehicles (V2V), infrastructure (V2I), pedestrians (V2P), and networks (V2N). As connected cars transform into self-contained cyber-physical systems, security has to be multi-layered to reckon with both the cyber and physical vulnerabilities of these smart mobility systems.
Automotive cybersecurity represents a real and significant financial and reputational risk for OEMs. For instance, the 2015 hack resulted in the recall of nearly 1.4 million vehicles and is estimated to have cost the manufacturer almost $600 million. In addition, there is the reputational damage, and its attendant financial consequences, with an overwhelming majority of consumers indicating that they are completely unwilling (28%) or at least quite reluctant (63%) to purchase cars from OEMs that have been hacked.
Auto OEMs have a huge opportunity to leverage cybersecurity as a brand differentiator and a key competitive advantage. There are, however, several challenges that have to be addressed before they can get there.
First, OEMs have a track record in safety, though not yet in cybersecurity. The primary challenge, therefore, will be to create a cybersecurity culture that extends across OEM operations and the entire value chain.
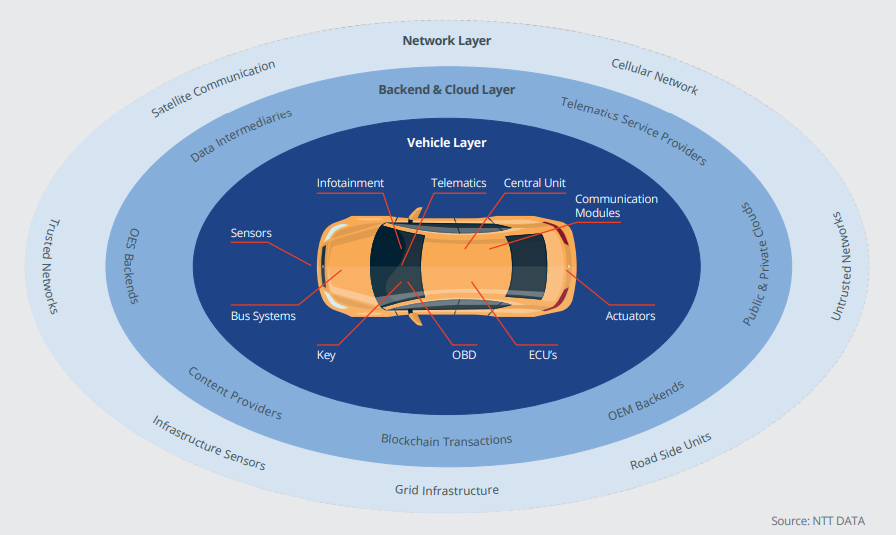
Two, securing the connected car ecosystem is a complex process covering multiple layers and numerous discrete but interconnected components. Any weakness in a single layer or component can potentially be exploited to compromise the entire system. Then, there is also the added complication of ensuring that these security provisions and protocols remain updated and functional across the lifecycle of the product.
Three, OEMs rely on a long and complex supply chain for systems, software and hardware components that go into the manufacture of their vehicles. Vulnerabilities can enter the system from any one of the nodes, which takes us back to the first point that cybersecurity culture, process and best practices have to be applied across the extended value chain in order to ensure effective security. Even so, most organizations (56%) still do not impose cybersecurity requirements for products provided by upstream suppliers.
And four, cybersecurity in the automotive industry is still an unstandardized anomaly. Automotive suppliers often have to resort to software adjustments in order to align the security requirements of each OEM with that of their own products. That probably explains why nearly three-quarters of respondents in the Synopsis-SAE survey express serious concerns about the cybersecurity posture of technologies supplied by third parties.
Today, only 19% of organizations address issues of security and vulnerabilities in the requirements and design phase. Security by design, therefore, will have to become an overarching priority for the automotive industry as systems become increasingly complex and threats become more sophisticated. The focus has to be on creating a culture of security that prioritizes cybersecurity best practices across the entire product development life cycle and the supply chain.
Collaboration will also play a critical role in the industry’s approach to understanding and mitigating cybersecurity risks. As we detailed in the previous article in this series, companies from across the shared mobility spectrum are partnering to share costs as well as risks in the development of connected automotive technologies. Initiatives like Auto-ISAC (Automotive Information Sharing And Analysis Center), a global alliance between suppliers, commercial vehicle companies and automobile manufacturers, facilitate the sharing and analysis of cybersecurity intelligence and risks to collectively enhance vehicle cybersecurity capabilities across the industry. In 2016, the alliance released a high-level best practices document that covers organizational and technical aspects of vehicle cybersecurity including security by design, risk assessment and management, threat detection and protection, incident response, collaboration and engagement with third parties, governance and awareness training.
Similar high-level guidance documents, standards and principles have also been published by institutions such as SAE International, a global standards development organization, and ENISA, the European Union Agency for Cybersecurity. In 2016, SAE released the SAE J3061 Cybersecurity Guidebook for Cyber-Physical Vehicle Systems defining the defined the world’s first automotive cybersecurity standard. ENISA published its first good practices and recommendations study on automotive cybersecurity in 2017, following it up with a new study in 2019 that broadens the scope to semi-autonomous cars and V2X communications.
Connected cars have a lot of potential to reduce road accidents and improve traffic efficiency. In doing so, new MaaS businesses and business models will emerge to serve customers who want just-in-time, flexibility transportation options which are cost effective and kind to the planet.
However, cybersecurity is the biggest hurdle to realizing that potential. This year, more than 10 million connected cars will be added to roadways worldwide, putting the auto industry’s cybersecurity capabilities on trial. The industry’s performance in securing connected vehicles at scale will be a key milestone on the road to full autonomy and that goal will be heavily determined by the OEMs' desire to adopt and partner with specialist suppliers of mobility security solutions.