
As any mobile developer knows, APIs are the foundation of any mobile app strategy. They allow developers to quickly and efficiently access the data and functionality they need to build amazing apps. This article outlines a 5 step checklist to make sure your mobile platform is adopting best practice security.
As mobile app developers increasingly rely on APIs, they also open themselves up to new security risks. As a result, API channels are a primary attack surface that bad actors frequently target. In fact, a recent study found that 63% of all Android mobile apps are vulnerable to attack.
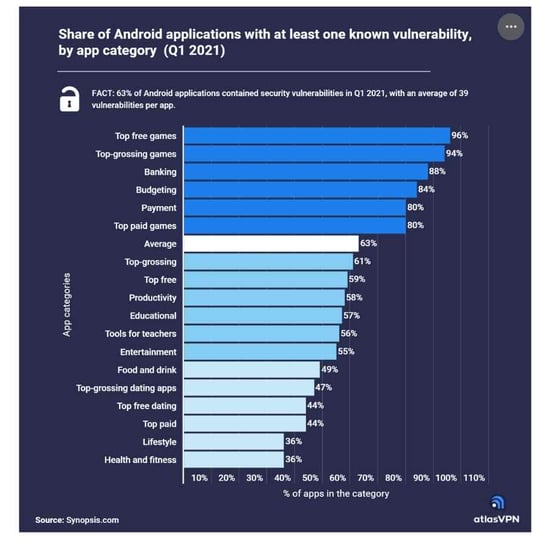 (Image source: atlasvpn.com)
(Image source: atlasvpn.com)
That's why mobile developers need to take steps to protect their APIs. Here are five best practice tips for doing just that:
1. App Integrity
If you're developing a mobile app that relies on a backend API or services, protecting your API from malicious or unauthorised access is vital. App attestation is one way to ensure that only genuine, tamper-free versions of your mobile app can access your API.
There are various ways to implement app attestation, but one common approach is to make use of a cryptographic signature of your app that can be verified. It's important that the verification is not done inside the mobile app itself or else attackers will manipulate it. The off-device verification should create a signal that can be passed to the server with the API request such that the server will first check verification result. If the signal is 'good', the server has confirmed that the app has not been tampered with and is then authorised to use the API.
2. Device Integrity Checks
Device integrity checks are an essential part of protecting the APIs used by your mobile app. By verifying that a device is not rooted or jailbroken, you can ensure that the operating system has not been tampered with or the device compromised, although it should be noted that in some markets and geographies, root/jailbreak is not a clear indication that a hacker is present and so more nuanced detections are needed. Additionally, checking for the presence of instrumentation frameworks such as Frida can help you to identify devices that are being used to manipulate data in or communications to/from the app.
3. Channel Integrity
When building a mobile app, protecting your API communication channel from Man in the Middle (MitM) attacks is important. One way to do this is through dynamic certificate pinning. This technique is based on regular certificate pinning to create a unique fingerprint for each SSL certificate your app trusts. In other words, when your app makes an API request, it will compare the server's SSL certificate against the pinned certificates. If there's a match, then the connection is considered secure. However, if the certificates don't match, the app will assume that it's under attack and abort the connection. Dynamic certificate pinning provides an extra layer of flexibility and security for your mobile platform by enabling pinned certificates to be instantly updated into all of your deployed apps if your certificate is compromised or you just want to rotate the pins.
4. Credential Integrity
User credentials, in the form of usernames/passwords or user authentication tokens, are the primary method for your customers to identify themselves to your mobile and/or your backend servers. There is much talk about moving to passwordless access for digital services but this is unlikely to happen soon. In the meantime, the important thing is to ensure that user credentials can't be abused at scale by bots and scripts which automate the process of logging to your accounts. These credential stuffing attacks capitalize on the fact that many customers use the same password on multiple platforms and, rather than advising them not to do it, a more effective method is to require a second, independent factor to be presented alongside the user credentials. In the case of mobile, this typically means something that proves the login request comes from your genuine mobile app, thus enabling you to block all automated login attempts.
5. Service Integrity
Protecting your service integrity allows you to protect your digital service from being attacked through exploitation of vulnerabilities in your platform. Much as there is not such thing as bug-free software, there is also no such thing as a vulnerability-free API. As hard as you work to track down and remediate these vulnerabilities, there is always more to do. This is why shielding your service from attacks aimed at exploiting vulnerabilities is such an important security layer; it allows you to continue vulnerability hunting safe in the knowledge that your services are safe from attack.
Review these 5 tips against the security arrangements you currently have in place for the APIs that service your mobile apps. And don't forget to consider 3rd party APIs which are called directly from your mobile app. Please get in touch if you want to talk to one of our security experts.