
In today's digital landscape, securing mobile apps and APIs is of paramount importance. Among the various security solutions available, Approov stands out as truly unique. What sets Approov apart is its combination of Mobile App Security and Mobile API Security, within a single product. With this innovative approach, Approov enables the lockdown of the Mobile API solely to clean mobile devices running authentic instances of the mobile app that have passed the Approov remote mobile app attestation process. This continuous verification process ensures the device and mobile app integrity, without any impact on user experience.
One of the key advantages of Approov over its competitors is the ability to remove hard-coded secrets from mobile apps by utilizing the remote mobile app attestation guarantees. These guarantees enable secure delivery of secrets just-in-time to be used in an API request, but only to valid instances of the mobile app that have passed the attestation. Subsequently these secrets are protected with Dynamic Certificate Pinning to protect attackers from intercepting the API requests to extract them, replay/modify the API request, enumerate all API endpoints to be able to build a bot or make one-off API requests from outside the mobile app.
An exceptional aspect of Approov's approach is that it does not require the mobile app binary to undergo any processing, whether locally or in the cloud, to inject code to provide Runtime Application Self Protection (RASP). Thus there is no need for Code Obfuscation or Code Hardening techniques to be applied to the mobile app to safeguard any injected third-party RASP code from being reverse engineered with the goal of bypassing its functionality or removing it entirely. You may still want to use these same techniques on your own code to safeguard the intellectual property on it or due to any concerns with business logic exposure, but if used to safeguard secrets then you may get yourself a Maginot line, a false sense of security. Instead, Approov provides an SDK that is heavily obfuscated and hardened, empowering your mobile app with RASP capabilities that go beyond traditional RASP solutions. This is achieved by incorporating remote mobile app attestation, API lockdown, dynamic pinning and runtime secrets Integrating the Approov SDK into your mobile app is a breeze - simply add it as a dependency and initialize it with just a few lines of code.
Approov Mobile App and API Security vs Competitors
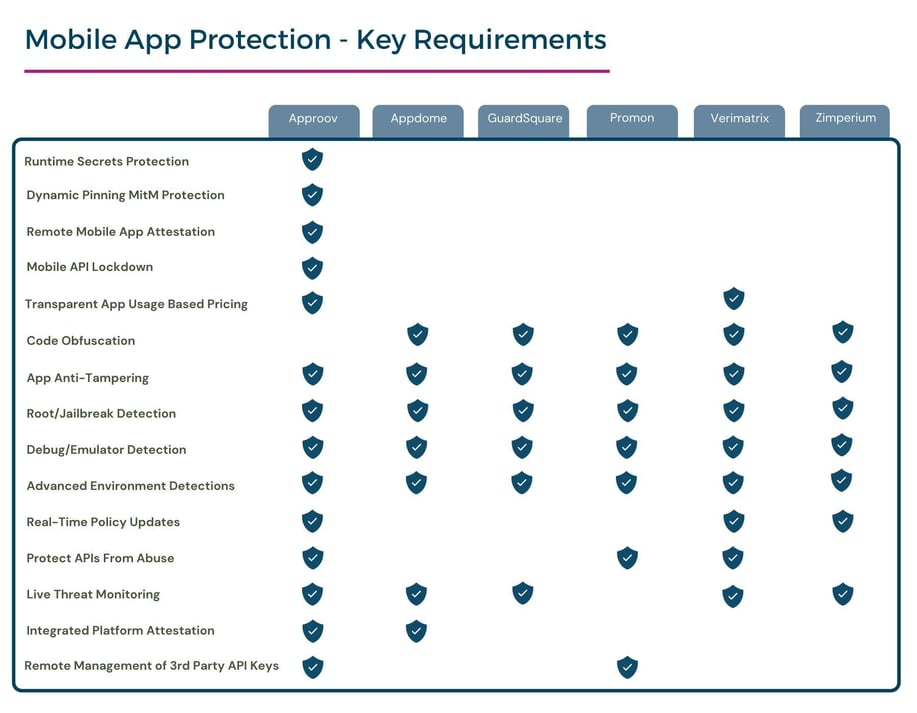
When comparing Approov against competitors such as Appdome, Guardsquare, Promon, Verimatrix, or Zimperium, it becomes evident that Approov's distinct features give it a competitive edge. Approov stands out from its competitors in Mobile App security and API security due to its four distinct and innovative features: Remote Mobile App Attestation, Runtime Secrets, Dynamic Certificate Pinning and Mobile API lockdown. This set of features is what makes Approov a very distinct solution for security-conscious individuals and organizations when they are comparing Approov vs Appdome, Approov vs Guardsquare, Approov vs Promon, Approov vs Verimatrix or even Approov vs Zimperium.
Approov stands alone as the only solution able to offer end-to-end security for mobile apps and APIs in a straightforward and efficient manner. It allows mobile app developers to remove hard-coded secrets from their mobile apps and utilizing remote mobile app attestation to securely deliver them just-in-time of being required to make the API requests, while detecting any runtime reverse engineering attempts or MitM attacks. This approach eliminates the possibility of attackers accessing your secrets, effectively fulfilling the same goals as Code Obfuscation, Code Hardening, and embedded RASP.
The subsequent sections of this article will delve further into the specifics of how and why this is accomplished.
Remote Mobile App Attestation vs Code Obfuscation and Code Hardening
Code Obfuscation and Code hardening in a mobile app are often used with the main purpose of hiding secrets, preventing reverse engineering and MitM attacks to steal such secrets. Code Hardening is also used to protect code injected in the mobile app to provide Runtime Application Self Protections (RASP) capabilities. Approov takes a different approach at tackling these same attack vectors:
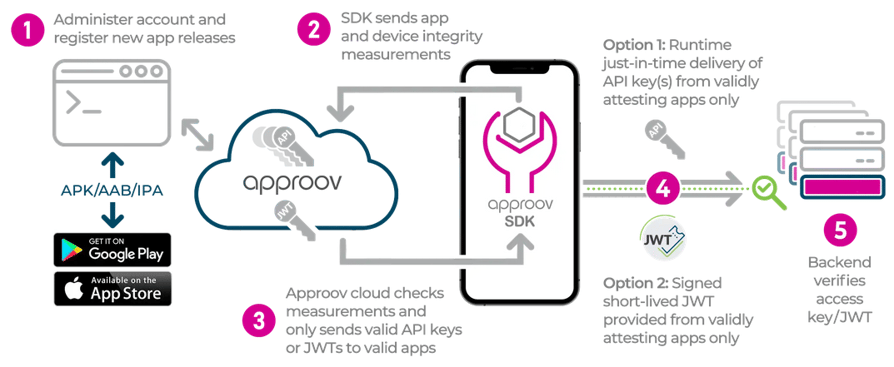
Instead of relying on code obfuscation, code hardening and embedded RASP capabilities to protect secrets from being extracted by attackers, Approov provides Runtime Secrets (3, 4 - option 1), that allows mobile app developers to remove secrets from their mobile applications code and have them delivered at runtime only to genuine instances of their mobile apps that pass the Approov remote mobile app attestation process (2, 3), which only requires the mobile app developer to register the mobile app release with Approov (1), instead of having to upload it to a cloud service to inject the code for RASP, with the subsequent need for code obfuscation and code hardening to secure the injected code.
Furthermore, the use of code hardening to hide the code injected in the developer mobile app to provide RASP capabilities is replaced with the Approov Remote Mobile App Attestation (2, 3), that relies instead on the Approov SDK to execute non replayable challenges provided by the Approov cloud service to determine the device and mobile app integrity:
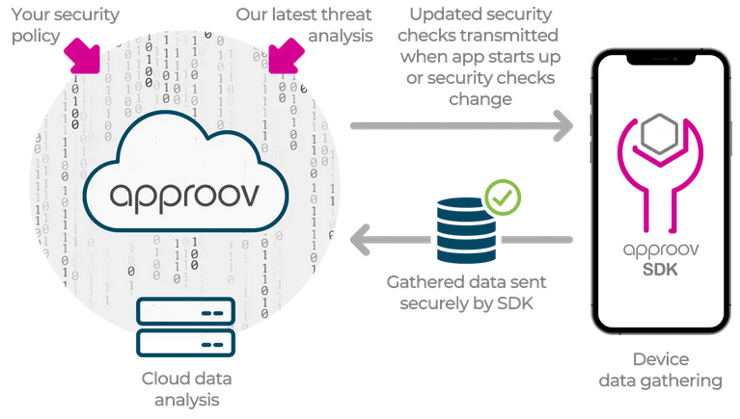
Approov’s Remote App Attestation provides a crucial advantage over traditional RASP solutions. Unlike in-app security policies that can be manipulated by attackers using instrumentation frameworks, Approov's attestation decisions are made in the cloud service, removing the decision process of the mobile app itself. Additionally, Approov offers configurable security policies at runtime, enabling mobile app developers to adjust their security posture, while allowing Approov to add new security policies to mitigate new zero-day threats. While this feature is not exclusive to Approov, it serves as an important distinction in terms of making decisions about a security policy.
Dynamic Certificate Pinning
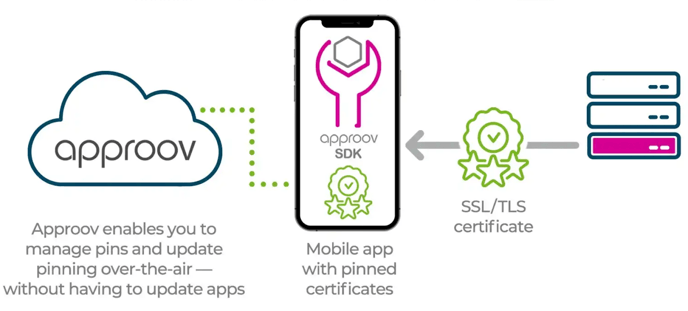
Another noteworthy feature of Approov is Dynamic Certificate Pinning. Leveraging its remote mobile app attestation capabilities, Approov facilitates secure over-the-air updates that include new security policies, runtime secrets, and API domain public key pins. This allows for out-of-the-box certificate pinning implementation as part of the Approov integration, safeguarding API requests against man-in-the-middle (MitM) attacks without the typical limitations of static pinning. Unlike static pinning, which requires a new mobile release to update the pins, Approov pins can be dynamically updated over-the-air, eliminating the need for mobile app updates. This ensures that backend certificate rotations can be instantly and smoothly handled without causing disruption to mobile app users.
Mobile API Lockdown to Genuine Instances of a Mobile App
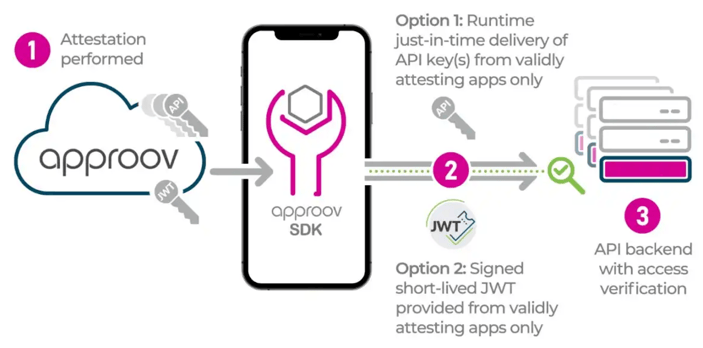
In addition to its other features, Approov offers the option to lock down the API backend for the mobile app to genuine instances of the app, the ones that pass the remote mobile app attestation (1). This is achieved by checking a JWT (3) in the header of each API request. (2) The JWT is provided by the Approov cloud service to the Approov SDK, which automatically adds it to the header of the API request. A valid and non-expired JWT signals the API backend that the mobile app and device integrity have been successfully attested by the Approov cloud service. Conversely, an invalid JWT indicates that the API request cannot be trusted because the mobile app failed to pass the remote mobile app attestation. API requests without the Approov token need to be rejected by the API backend, because they weren’t originated from a genuine instance of your mobile app.
Conclusion
When comparing Approov to Appdome, Guardsquare, Promon, Verimatrix or even Zimperium, it becomes clear that Approov stands out as the only solution that offers a range of important features. Firstly, Approov allows you to remove secrets from your mobile app, provides out-of-the-box dynamic certificate pinning to secure your API requests, and locks-down your mobile app with your mobile API - all backed by the security guarantees provided by its unique remote mobile app attestation capabilities.
Secondly, a significant advantage of Approov is that it eliminates the need to upload your mobile app to any cloud service to inject code to secure it with RASP capabilities that make in-app decisions, which is susceptible to manipulation by attackers. This approach ensures that your app remains secure without compromising its integrity.
Additionally, Approov doesn't require any server side infrastructure to provide remote app attestation capabilities to your mobile app, saving you the hassle of maintaining and monitoring additional backend systems.
In conclusion, Approov’s unique and innovative approach to Mobile App Security and API Security makes it the only solution capable of providing end-to-end security to your mobile apps and APIs without the complexities associated with integrations that require uploading the mobile app binary or setting up additional infrastructure to your backend, that requires maintenance and constant monitoring to keep availability. By integrating the ApproovSDK into your mobile app, you gain access to advanced RASP capabilities that go beyond traditional solutions. This includes remote mobile app attestation, API lockdown, dynamic pinning, and runtime secrets. This integration process is straightforward allowing mobile app developers to add the Approov SDK as a dependency and initialize it with just a few lines of code.








